![]()
Tag Archives: two-factor authentication
LastPass Mitigates Newly Disclosed Phishing Attack
LastPass has mitigated the effects of a new phishing attack presented this weekend at ShmooCon.
Six things to think about in the new year
Here are six things to think about for this year, with business security strategy top of mind…
1. Artificial Intelligence keeping us safe online
Artificial intelligence and machine learning isn’t just about robot dogs and self-driving cars. The latest AVG Business anti-malware products contain a number of sophisticated neural learning and cloud-data collection techniques designed to catch malware earlier and more often. Expect to hear more through 2016 about how artificial intelligence will help transform security solutions to help keep malware at bay.
2. Certificate Authorities: beginning of the end
SSL continued to be a big talking point in 2015 with further vulnerabilities being disclosed. This year the debate will continue around certification, development of new open standards and easier choices for website owners. Every news story about certificate mismanagement, security mishaps, and data breaches puts Certificate Authorities under increasing scrutiny. For many small businesses, the website owners paying a Certificate Authority and submitting themselves to what can sometimes be an arduous verification and checking process, is cumbersome and unnecessary.
This is where technical alternatives like Let’s Encrypt (currently in beta) are bound to flourish.
Additionally, Google’s Certificate Transparency project will continue to identify rogue SSL Certificates through detections built into modern day web browsers, as Google continues to hold Certificate Authorities to account – helping keep us all safer.Lastly, with the promise of other solutions such as the Internet Society’s proposed DANE protocol, offering the ability for any website owner to validate their own SSL certificate and therefore bypass a Certificate Authority altogether, 2016 will be an interesting year to watch!
3. Malvertising, Ad Networks: shape up, or ship out
Malvertising is what happens when malware is served up to innocent web site visitors; it’s happening all too frequently and is caused by questionable third party relationships and the poor security of some online advertising networks. At the root of this problem is the “attack surface” of ever-growing, ever-complex advertising and tracking “scripts” provided by ad networks and included by publishers (often blindly) on their websites. The scripts are slowing the browsing experience and anyone who has installed an ad blocker recently will tell you they can’t believe how fast their favourite websites are now loading. Research conducted by The New York Times showed that for many popular mobile news websites, more than half of the bandwidth used comes from serving up ads. That’s more data from loading the ads, scripts and tracking codes, than the content you can see and read on the page!
Whatever the solution, one thing is for certain, Ad Networks need to shape up and address their security, otherwise 2016 may well be remembered as the year of Malvertising.
4. Augmenting passwords with extra security steps in 2016
The need for strong passwords isn’t going anywhere in 2016. There were reminders in 2015 that even having the world’s longest smartphone passcode doesn’t mean someone can’t figure it out.
This year, there will be growing use of extra steps to make accessing data safer. In 2015, Yahoo announced a security solution using mobile devices rather than a password for access, and we even saw Google include Smart Lock features that can use the presence of other nearby devices to unlock your smartphone. Two-factor authentication – using two steps and ‘something you have and something you know’ to verify someone’s identity – will continue to be popular for use by many cloud-based providers looking to avoid data breaches.
5. The Internet of Things needs security by design
Every device seems to be getting smart – in the home and in the office. You’re likely going to be using your smartphone as a “lifestyle remote” to control a growing array of devices. Being able to set the office temperature remotely, or turn on the kettle in the communal kitchen without leaving your desk may sound helpful, but the devices have the potential to give up WiFi keys. Every unprotected device that is connected to a network is open to hacking. Cyber criminals are probing hardware, scanning the airwaves, and harvesting passwords and other personal identity data from wherever they can. So the advice is simple: every connected innovation needs to be included in your business-wide security.
6. Update and upgrade or face the financial and legal consequences?
Upgrading and updating all your software, devices, gadgets and equipment remains a vital business issue. The Internet of Things is raising new questions about who is responsible for what in a legal sense. Who owns data? What happens when machines take “autonomous” decisions? Who is liable if something goes wrong? To take one extreme example, a police officer pulled over one of Google’s driverless cars in November for causing a traffic jam on one Californian highway by driving too slowly. Again, the lesson is clear. The simple rule this year is to ensure that your business software and systems are always using the latest update. Your life may not depend on it, but your livelihood might.
So these are my six “thinking points” as we head into 2016.
Here at AVG, we look forward to helping you keep security front and center for your business this year. For more information on AVG Business security solutions that keep devices, data and people protected every day, across the globe, visit http://www.avg.com/internet-security-business.
![]()
![]()
Santa’s Security Secrets
We all think we know Santa – where he lives (to the nearest Pole!), what he likes to wear (on one day of the year!) – but what do we really know about this mysterious character? What does he do during the rest of the year, what are his hobbies, where does he work on the other 364 days of the year, what is his ‘real’ name, and more importantly – who is on his naughty list?! None of these personal details have ever been revealed, and even in today’s connected world, Santa has managed to keep his identity a closely guarded secret – but how, and what best practices can we learn from our favorite festive character?
He wears the AVG Invisibility glasses
Santa saw AVG’s Invisibility Glasses in February and sent us a letter saying “Dear AVG, those Invisibility Glasses are just what I need to keep me invisible during the year. I have been a good Santa, and I hope you can help me out.”
The glasses make it difficult for cameras or other facial recognition technologies to get a clear view of Santa’s identity, so Facebook can’t automatically tag him in that embarrassing picture under the mistletoe, for example! We, of course, agreed to provide a pair, enabling Santa to travel the world without being tracked, seeing sights that would have been difficult to visit due to the number of people taking pictures to post online. Santa has provided us some pictures from his travels that we can share with you here…XXXX.



While not generally available yet, unless you’re Santa, the concept serves as a reminder to protect your privacy online. There are, of course, many other methods Santa uses to stay private – he has shared a few of them with us in this exclusive interview!
He stays away from social media
“There are hundreds of Santa impersonators on Facebook, but I – the real Santa – am nowhere to be found,” says Santa. Staying away from social media completely might be a challenge for the rest of us, but it’s worth thinking about the information we share via these channels at this time of year. Make sure to check your security and privacy settings to ensure you’re not exposing any information you’d rather not be. “You may want to think twice about posting those pictures of the latest high-tech gadgets you’ve been gifted too – you never know who might be looking!”
He still uses a POLARoid camera
“I never take selfies,” says Santa, “they may get leaked online and that could be awkward.” But with most of us now using our smartphones to take pictures, there are privacy issues you may not have considered. Aside from pictures getting into the wrong hands – the recent VTech hack which may have enabled hackers to steal children’s photos is an example – you might not know that smartphone photos are also often ‘geotagged’, meaning that others can find out exactly where your pictures were taken.
His sleigh is Wi-Fi free and disconnected
“Checking out if you have been good or bad is now even easier with people posting so much of their lives on their online profiles. I avoid being located, tracked or leaving things to chance by using an encrypted Virtual Private Network (VPN) when using the Internet,” says Santa. But It would be impractical for most of us to avoid the Internet completely. There are ways to make sure you’re surfing securely and privately though.
Secure your home Wi-Fi with encryption using a strong password. Also avoid public Wi-Fi hotspots when transferring personal details online during bank transfers for example, or follow Santa’s example and use a VPN. Phishing emails also tend to spike around the festive season as cybercriminals try to tempt us with too good to be true deals. If at any point you think the email is spam and fraudulent then do not open or click on any links, just delete the email!
He pays for everything with toys
Santa told us that his “route and present list is a closely guarded secret. I use very strong passwords and a reindeer for two-factor authentication”. If you’re doing last minute shopping online this year, it’s worth taking to time to remember good password practice – to save time, and a potential headache, later! This means using strong passwords that are different for each account, along with additional security codes or the ‘two-factor authentication’ Santa refers to where available.
So now you know a bit more about Santa and his security secrets – hopefully they’ll also help you to stay safe and secure this Christmas. Happy Holidays!
Image sources:
The British Foreign and Commonwealth Office, Erik (HASH) Hersman, TANAKA Juuyoh (田中十洋), Sreejith K, Brian Burk
![]()
![]()
Amazon ‘resets customer passwords’ as Black Friday approaches
Amazon has reportedly reset a number of customer passwords, causing some concern as Black Friday and Cyber Monday are just around the corner.
The post Amazon ‘resets customer passwords’ as Black Friday approaches appeared first on We Live Security.
![]()
Reclaim privacy with operational security says Snowden
Edward Snowden has been offering advice on operational security to ordinary people, advocating, among other things, two-factor authentication and encryption.
The post Reclaim privacy with operational security says Snowden appeared first on We Live Security.
![]()
iOS 9 boosts iPhone 6s and iPad Pro security with improved 2FA
Apple has announced that iOS 9 will launch on September 16th. The updated operating system will have even greater security features, including a stronger passcode and improved 2FA.
The post iOS 9 boosts iPhone 6s and iPad Pro security with improved 2FA appeared first on We Live Security.
![]()
Introducing the new Facebook Security Checkup
Earlier in August, the world’s largest social networking site, Facebook, unveiled their new Security Checkup feature.
The aim is to create a series of simple tools that help users control which devices are logged into Facebook, receive alerts when new devices log in and tips on creating a strong password.
Let’s take a look in more detail:
Log out of unused apps:
If you have multiple devices linked to your Facebook account, you may be surprised to see just how many apps have access to your account. Closely monitoring which apps have access to your account is a great way to help protect your account security and the privacy of your personal information.
It’s worth remembering that apps that have access to your Facebook account also have access to a lot of your personal information. Be selective about which apps you allow.
Login Alerts:
Setting up login alerts is a great way to help you manage access to your Facebook account. Used in conjunction with other security features such as Two-Factor Authentication, login alerts make it very difficult for any unauthorized party to gain access to your account. I’d highly recommend implementing both this and Facebook’s Login Approvals.
Password strength tips:
The final tool in the Security Checkup is some advice both for creating a strong password and also password safety advice.
The advice recommends using a password unique to Facebook, never sharing your password and avoiding dictionary or identifying words.
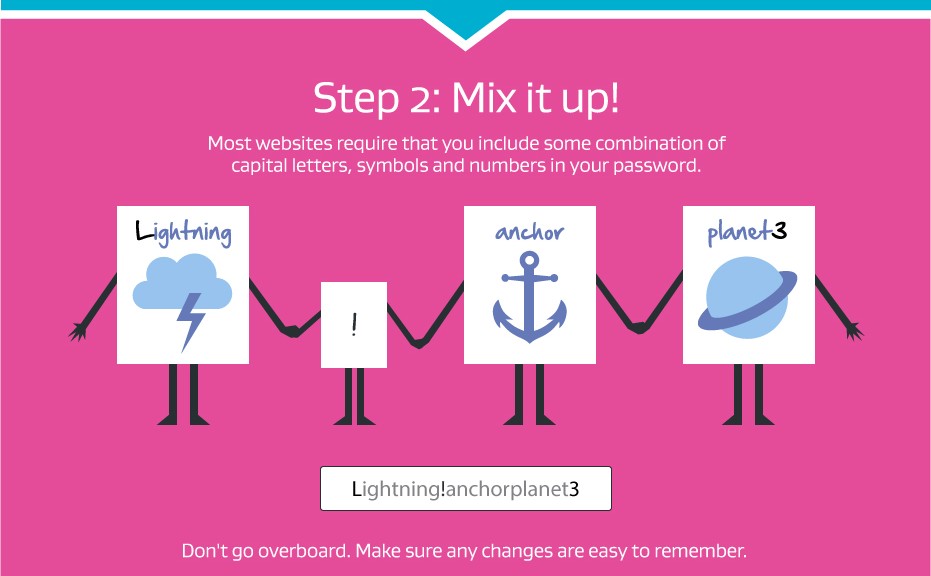
Your password is one of the most important parts of keeping all your online accounts safe, for more information on creating a strong, unique password that’s easy to remember, check out this infographic below.
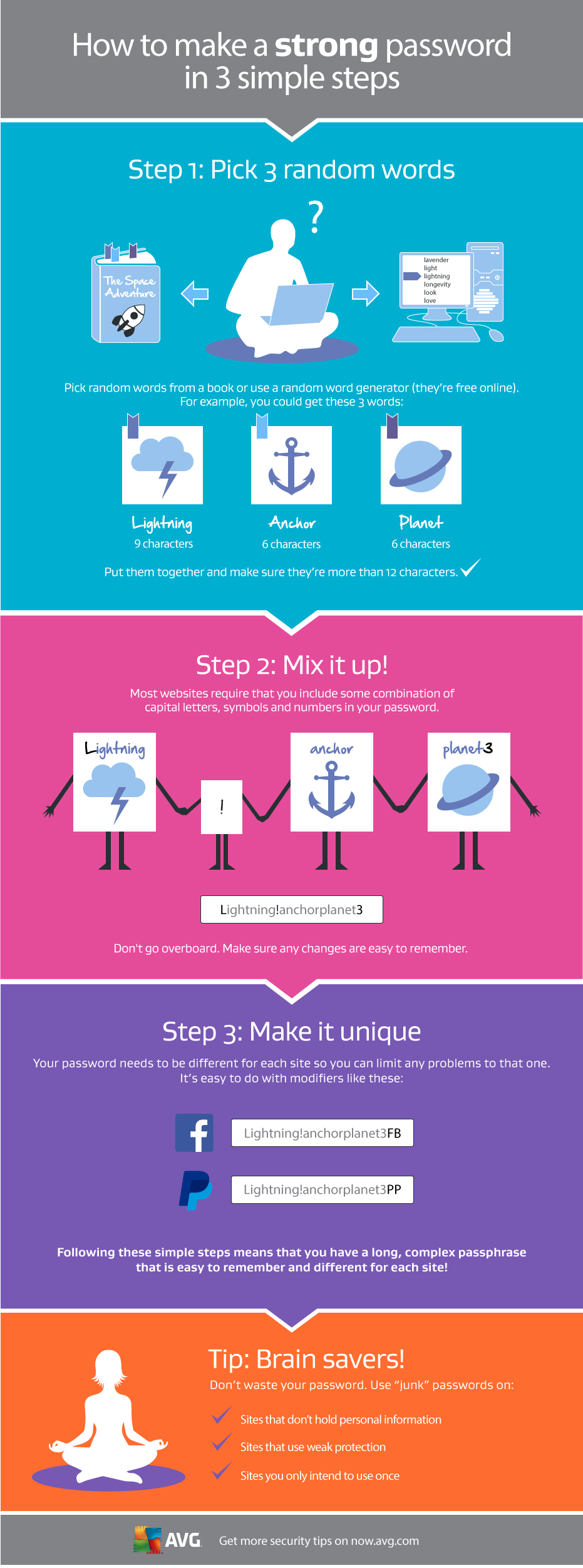
One-Time passwords: What you need to know
Most of us have dozens of online accounts, each of which should have its own unique password. Remember them all can be a bit of a headache, which is why some people have turned to password managers.
However, events in the last few months have shown that not all password managers are entirely secure, leaving people at odds when it comes to securing their online lives.
One trend that has been steadily gaining momentum is that of the one-time password. Forget having to remember your login for each account and instead have a strong, unique password sent directly to you whenever you need to log in.
When you want access to your account, a link is sent to you via email, SMS or in app and that can be used to log in. No password required.
Yahoo! Become one of the first household names introduce one time passwords a few months ago and you can see my colleague Tony Anscombe’s views on their implementation on his blog.
More recently, blogging site Medium has just rolled out the feature. They believe that one-time passwords are stronger than traditional means of authentication as they explain on their blog:
It sounds counterintuitive, but this is actually more secure than a password-based system. On most services, if someone guesses or cracks your password, they gain access to your account until you change your password, which might not be for a long time. You might never know that they have access. With this email-only system:
- You’re automatically notified when someone tries to sign in.
- The sign in link expires after a short amount of time.
- The sign in link can only be used once.
Are there any downsides?
One-time passwords do a great job to help avoid many of the common issues with real passwords such as:
- Weak passwords
- Reusing passwords across multiple sites
- Writing passwords down
- No warning when someone else has access to your password/account
There is some room for vulnerability in the current system.
Encryption – Emailing a link that can provide unlimited account access, should of course be done in an encrypted fashion. However, this isn’t always possible and transmitting it in plain-text over email or SMS could be a major security vulnerability.
Degrades security – A potential downfall for one-time passwords, especially with Mediums implementation, is that any one-time password account is only as secure as your authentication email account.
For example, it would be useless to manage every one of your online accounts with a one-time password, but only secure your email with a weak password (as many people do). Remember, your email password should be the strongest of all your passwords as it can hold the key to the rest of them. One-time passwords make this even more pertinent.
Forwarding – Obviously it is unlikely, but with the current implementations, anyone with the link would be able to access the account. If you forwarded an email by mistake or pasted the link in the wrong place, then this could leave you vulnerable.
Some verification that the link is being clicked within the correct email account would be an added bonus so that the link would be a big bonus.
Alternatives
So while it is up to you whether or not you want to secure your online accounts with one-time passwords, if you are looking to improve the security of your online accounts I can recommend deploying Two-Factor Authentication.
Two-Factor Authentication is perhaps the simplest way to prevent unauthorised access to your online accounts and is very low risk. For more information on Two-Factor Authentication, check out the video below:
Snapchat rolls out two-factor authentication
The feature, known as ‘login verification’, is a way that users can help protect the privacy of their Snapchat accounts.
Two Factor Authentication is a way to help secure your online accounts by adding another step when you login. With Two-Factor Authentication, your regular password won’t be enough to gain access to your account. You will also need a code which is sent to your mobile device, either in form of a text message or via an app.
In Snapchat’s case, the first time an account is accessed from a new device, Snapchat will require a code sent via SMS to the mobile number registered on the account. This code can then be used to access Snapchat normally. Afterwards, the authorization will not be required on that device again (unless you instruct Snapchat to ‘forget’ the device.)

For more information on two-factor authentication, check out the video below from AVG Academy.
How to enable login verification on Snapchat
As detailed in Snapchat’s support page, here’s how to enable login verification in the app:
- Tap the ghost icon at the top of your camera screen
- Tap the Settings gear in the top right hand corner of your Profile screen
- Tap ‘Login Verification‘ under the ‘My Account’ section
- Tap the ‘Continue‘ button
- Enter the verification code sent to your mobile phone and tap ‘Continue‘
Once you have completed the login verification process, your device will remain a verified device until you elect to forget it.
![]()
![]()