In the first article of our series “Ranking of Attacks Aimed at Businesses”, we’ll introduce you to the top security threats aimed at companies and give you some tips on how you can protect yourself!
In the first article of our series “Ranking of Attacks Aimed at Businesses”, we’ll introduce you to the top security threats aimed at companies and give you some tips on how you can protect yourself!
Staying up-to-date with security is an undertaking and requires effort and commitment. As technology develops and evolves, it is easy to fall behind. Cyber-criminals, on the other hand, are always ahead of the game and are constantly looking to exploit new vulnerabilities that accompany these innovations.
To protect yourself, it is extremely important to keep up with cybersecurity trends. Every year, the RSA publishes a report on the current state of cyber-crime that summarizes the hacking methods that are trending among cyber-criminals. Being aware of these trends is vital for IT security in companies. (The RSA is a group of American IT security experts that developed the RSA public key cryptography algorithm, and later renamed their computer network and security company the RSA.)
Attacking Your Wallet
Today, it is extremely easy to complete transactions on mobile devices, which is part of the reason this is an area that has quickly gained popularity among cyber-criminals.
More and more companies are setting-up services based from mobile phones. This benefits both customers (e-commerce apps, payment platforms, etc.) and employees, whose work is increasingly dependent on these devices. However, these conveniences also make everyone involved more desirable and attractive to cyber-criminals.
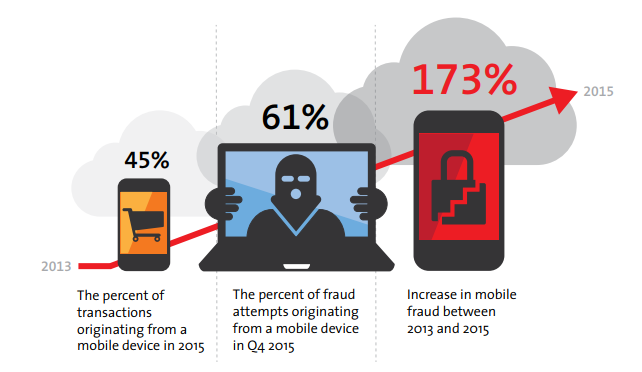
Although these transactions are convenient, there is a lot of fraud associated with these channels. Since mobile devices have not been around as long as other devices, like computers, security technology is not as advanced and they are usually less protected.
In 2015, the RSA detected that 45% of transactions, and 61% of fraud attempts, took place in mobile devices.
In response to this, an interest in biometric identification systems has emerged, which identify users by analyzing some aspect of the body, or physical behavior.
There is an emerging special interest in biometric identification systems
Today, this technology can be found in facial recognition, fingerprint and iris scanners, and less commonly in voice or signature recognition. In addition, it is being investigated how other biometrics can be used for identification like our typing patterns, movement patterns, heart rate, and sweat levels.
According to the report of RSA, more than 90 % of banks are currently exploring the use of biometrics in their mobile applications (or intend to do so) within the next nine to twelve months. Many companies are following the same path. In fact, the future of authentication seems to be a mix of these systems with traditional ones, such as PINs and passwords.
Using a combination of both is the best option to ensure security in the future. More than one billion transactions, both online and offline, were influenced by mobile attacks in 2015.
If you want to boost your business’s cybersecurity, it is fundamental to invest in an advanced cybersecurity solution that will allow you to manage, control and protect your entire technological park from one place.
The post Ranking of Attacks Aimed at Businesses: Protect Your Wallet appeared first on Panda Security Mediacenter.