
Cyber-attackers are always finding new ways of bypassing the protection systems installed on computers in order to avoid detection and steal user data. In that respect, Black Hat hackers have always turned to malware-based attacks (phishing, network worms, or the dreaded Trojans with ransomware as the most dangerous example) to reach their goals: break into companies to steal credentials and huge amounts of other data in exchange for a ransom… At least, until now.
PandaLabs has recently detected a quite clever attack targeting a company in Hungary. What makes it so special? Well, the attack does not use any malware as such, but scripts and other tools belonging to the operating system itself in order to bypass scanners. This is just another example of the increased self-confidence and professionalization we have been observing among cyber-crooks in recent months.
Analysis of a malware-less attack
First, and as has become the norm in the latest security incidents analyzed at the lab, the attack starts with the attackers launching a brute-force attack against a server with the Remote Desktop Protocol (RDP) enabled. Once they get the computer’s login credentials, they have complete access to it.
Then, the first thing that the attackers do is run the sethc.exe file with the parameter 211 from the computer’s Command Prompt window (CMD). This turns on the system’s “Sticky Keys” feature. We are sure you have seen this message before:
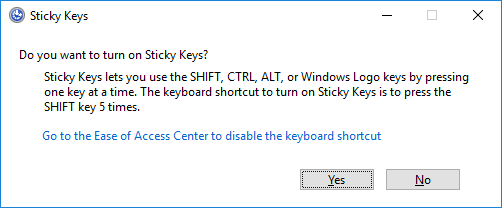
Next, a program called “Traffic Spirit” is downloaded and run. “Traffic Spirit” is a traffic generator application which in this case is used to make extra money out of the compromised computers.
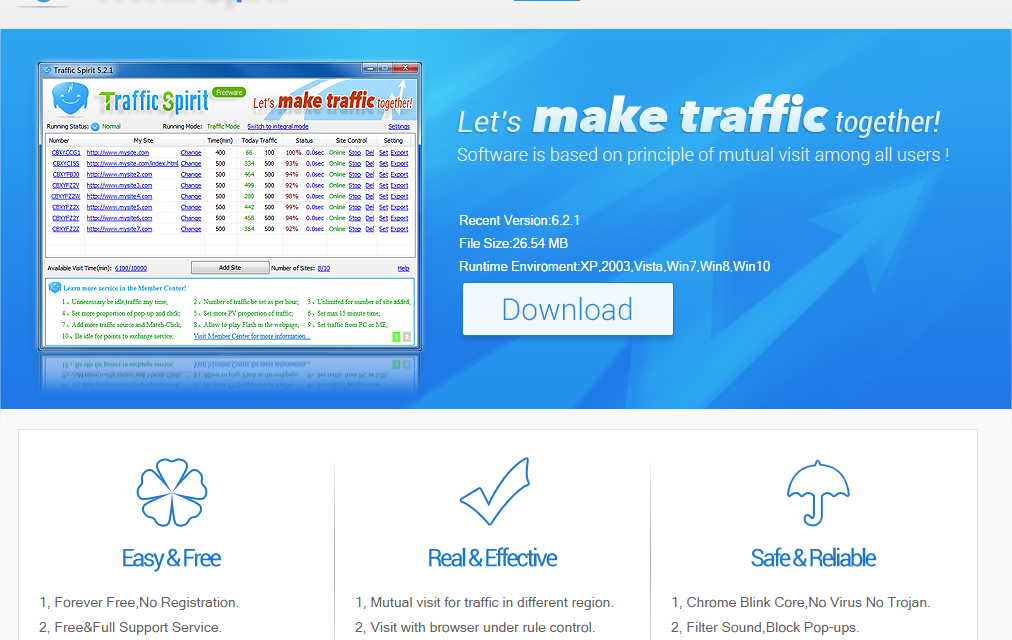
Then, a self-extracting file is launched that uncompresses the following files in the %Windows%cmdacoBin folder:
- registery.reg
- SCracker.bat
- sys.bat
The attackers then proceed to run the Windows registry editor (Regedit.exe) to add the following key contained in the registery.reg file:
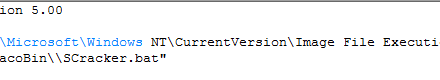
This key aims at ensuring that every time the Sticky Keys feature is used (sethc.exe), a file called SCracker.bat gets run. This is a batch file that implements a very simple authentication system. Running the file displays the following window:

The user name and password are obtained from two variables included in the sys.bat file:
![]()
This way, the attacker installs a backdoor on the affected machine. With this backdoor, the attacker will be able to connect to the targeted computer without having to enter the login credentials, enable the Sticky Keys feature (for example, by pressing the SHIFT key five times), and enter the relevant user name and password to open a command shell:
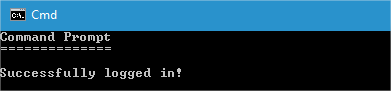
The command shell shortcuts will allow the attacker to access certain directories, change the console color, and make use of other typical command-line commands.
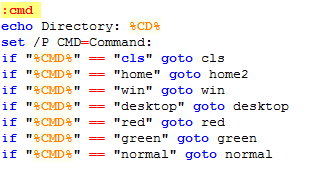
However, the attack doesn’t stop here. In their attempt to make as much profit as possible from the targeted company, the attacker installs a bitcoin miner to take advantage of every compromised computer for free money. Bitcoin mining software aims to use the victims’ computer resources to generate the virtual currency without them realizing. A cheap and very effective way to monetize computer infections.
How does the Sticky Keys feature aid cyber-crooks?
If an attacker can actually access a targeted computer via an RDP connection, what do they need a backdoor for? The answer to this question is quite simple: By installing a backdoor on the affected machine, even if the victim realizes that their system has been compromised and changes the Remote Desktop credentials, all the attacker has to do is press the SHIFT key five times to enable Sticky Keys and run the backdoor to be able to access the system again. And remember, all of this without running malware on the affected computer.
Adaptive Defense 360, Panda Security’s advanced cyber-security solution, was capable of stopping this targeted attack thanks to the continuous monitoring of the company’s IT network, saving the organization from serious financial and reputational harm. Protect your corporate network with the security solution that best adapts to your needs.
The post Sticky Attacks: When the operating system turns against you appeared first on Panda Security Mediacenter.