An unusual DDoS amplification attack was carried out 10 days ago against many of the Internet’s 13 root name servers, the authoritative servers used to resolve IP addresses.
Tag Archives: Domain Name System
Exploit Kit Using CSRF to Redirect SOHO Router DNS Settings
French researcher Kafeine has found an exploit kit delivering cross-site request forgery attacks that focus on SOHO routers and changing DNS settings to redirect to malicious sites.
Secure your DNS to avoid losing business – Part 3
What happens if someone “owns” your DNS records
The direct consequence is that suddenly when contacting domain.com and all its subdomains (www, mx, ftp, etc.), some other servers owned by the new owner (legal or attacker) answer.
This disruption in normal operation means a loss of reputation, loss of market share, loss of trust from your customers and last but not least, financial loss for your business.
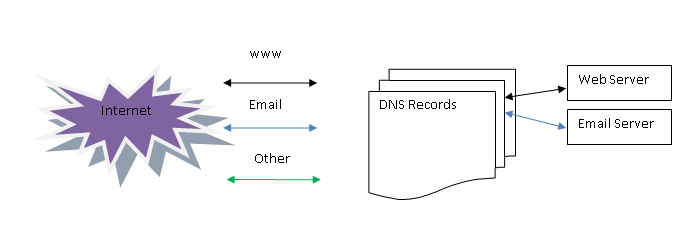
Unaltered DNS records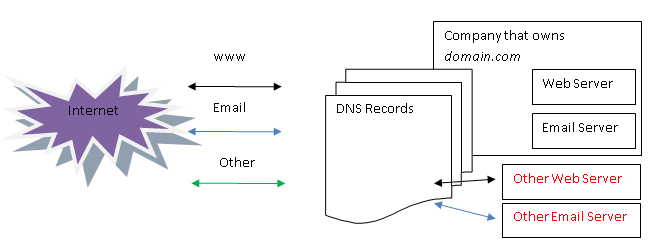
Altered DNS records
As can be seen in the above illustration, from the moment in which the DNS records are altered, the company that owns domain.com will no longer control where the traffic goes. The new owner can set up his web server to serve www.domain.com and his email server to serve mx.domain.com. Yes, this means that he can receive all email traffic for that domain.
Owning a black-white list can have even more consequences: the new server can serve whatever fits its needs. Either block any request reporting back that the item should be blacklisted (valid web sites, emails, files, etc.) or allowing everything (marking as good any malicious website, email, file). Fortunately, in such services there are many other controls that make such a task pretty complex.
What can you do to secure your domains?
Yes, there are things which you can do to prevent an attacker from taking ownership of your domains.
Lock your domains
Domain Lock or Registrar Lock is a status which can be set to a domain. When set, the following actions are prohibited by the registrar:
- Modification of the domain name, including:
- Transferring of the domain name
- Deletion of the domain name
- Modification of the domain contact details
Renewal of the domain name is, however, still possible when this flag is set.
Unfortunately, not all registrars support this functionality. If you want more security, you should choose a registrar that supports this feature. This functionality usually doesn’t come for free, but the price is not very high (10$-50$/month) and it is worth paying, especially if you have a large website or company.
Secure your domain administration information
All registrars allow entering contact persons for various functions. For example, there are some contacts for changing the IP address or deleting the domain and some others for paying the subscription. Make sure you separate them. Also, make sure that you have a contact email address that is not hosted at the respective domain. Otherwise, if something happens to the domain, you can’t access your email anymore. Remember that all traffic goes to the new owner, including your emails.
If you use some free email servers like Gmail, Yahoo or others, make sure to activate two factor authentication for those accounts.
Set up a good password and make sure you don’t use the address hosted on the domain you try to protect as the recovery email address.
Make it harder for the attacker to get access to your account.
If you have multiple domains, it would be better to host them at different registrars. If one goes down, you can at least use the other ones.
The post Secure your DNS to avoid losing business – Part 3 appeared first on Avira Blog.
Secure your DNS to avoid losing business – Part 2
What happens when DNS doesn’t work?
Of course, having a non function DNS causes problems. We have to differentiate between two types of disruptions which have as consequence that the DNS resolution doesn’t work anymore: unintentional and intentional.
Unintentional disruption
In this case, nobody intentionally caused the issue that prevents the DNS service to function correctly. This can happen because of a configuration error or a hardware failure. A good IT administrator can deal with it rather fast, especially if there is no change in the IP addresses or domain names (it is about restoring). If there are IP or name changes, even if the problem gets fixed on the source quickly, it takes usually minimum 24h for the changes in the DNS to propagate to enough servers so that someone can feel the difference. Propagation is the way DNS servers exchange information between them so that as many as possible services know how to resolve a certain domain to its IP address. This delay can cause serious problems to your customers and visitors.
Intentional disruption
There are, however, cases when DNS errors are caused intentionally by persons or organizations who want to produce damages to the owner of a domain. This happened many times in the past and even some big companies where hit by this problem (Facebook, Google, Twitter, AVG, Avira, WhatsApp, etc.).
Let’s see how someone can change your DNS records.
Registrar manipulation
DNS is a service, and as any service, there has to be a service provider that offers the infrastructure that host the records (the tables that map a name to an IP address). Such service providers, usually called registrars, are all big ISPs like Comcast, 1&1, Network Solutions and so on. If one of them gets hacked then it is possible to alter the DNS records for any of the domains hosted there. In the past 12 months a couple of big registrars were hacked and this resulted in downtime for many domains.
This attack has potentially global consequences since, most of the time, authoritative DNS servers are affected.
Cache poisoning
DNS cache poisoning or DNS Spoofing, is a complex attack because it targets a certain audience. It is directed against the users that are dependent on the attacked service. This can happen after an attacker is successfully injecting malicious DNS data into the recursive DNS servers that are operated by many other ISPs. The attacker usually chooses the DNS servers that are the closest to the targeted users from a network topology perspective. The best way to prevent this type of attack is to use DNSSec. If this is not possible, another way to protect the DNS records is to restrict their propagation to only servers that prefer to get fresher information from the Internet instead of caching an entry for a long time (in order to save bandwidth and time).
Legal DNS takeover
While related to the first case which is illegal, this takeover is completely legal (it is enforced by a court order) and it is performed by the registrar directly without consulting the owner of the domain. Recently, in an incident with domains hosting malware in the U.S., Microsoft managed to obtain legal custody of the DNS entries of the well-known service NO-IP Managed DNS. This had as consequence that thousands of innocent users who used No-IP’s service were no longer able to resolve their domains. The customers were using a form of <user-dns>.no-ip.com and several other hosts to reach their own domains. Without no-ip.com, the base domain, no subdomain worked anymore.
This can happen at any time and in any country because the laws are (still) very blurry in regards to cybercrime and what is allowed and what not.
The post Secure your DNS to avoid losing business – Part 2 appeared first on Avira Blog.
Secure your DNS to avoid losing business – Part 1
What is DNS and where is it used?
What many don’t realize is that there is much more behind it than just name to IP translation (called DNS lookup) and the other way around (that is called reverse DNS lookup).
There are hidden services which are critical for the proper functionality of the Internet like mail, ftp, web – just to name the most well-known. All these services are used every day by billions of people, devices and online services around the world without even thinking at them. The only time when they are aware of their existence is, when they don’t function anymore. But before going into this, let’s briefly go through the most important of them: email and web.
Mail transfer agents use DNS to find out where to deliver e-mail for a particular address. The domain to mail exchanger mapping provided by MX records (Mail eXchange) is another example of how DNS works. MX represents the entity (mail server) that can receive email for a domain. The MX record is used by mail servers to exchange emails and it is configured as a subdomain like mx.domain.com. For example, if a user [email protected] wants to send an email to [email protected], the two servers must communicate via their MX records (domain1.com connects to mx.domain2.com), negotiate and agree on certain parameters and then finally exchange the email message.
The first and most important thing that must happen is that the servers are able to contact each other. When trying to contact mx.domain2.com, the mail transfer agent running on domain1.com must be able to locate domain2.com (this is called A-Record). If the DNS resolution for a domain doesn’t work at all (the name to IP address translation doesn’t work) then it is impossible for that domain to receive any emails.
WWW
Ever wondered why do you have to almost always put a “www.” in front of a domain so that you can view its website? “www.“ is actually a subdomain for the main domain and it was historically chosen as an acronym for “World Wide Web” or simply said, the website of that domain. Same as for the email, if the main domain doesn’t get found, then you usually can’t see the website anymore.
Other uses of DNS
There are also other uses of the DNS which are even more hidden than the two mentioned above. Best example for such a service built on top of the DNS are white- and black-lists used to filter good and bad domains, respectively. A service makes a specially created query to a certain domain and get back an answer in form of an IP address (that’s what DNS does, right?). Many services use 127.0.0.1 for when the address is in the list and 127.0.0.2 when the address is not in the list.
Now you know exactly what DNS is used for and where. In our next part we will talk about what happens when DNS doesn’t work, so stay tuned!
The post Secure your DNS to avoid losing business – Part 1 appeared first on Avira Blog.