At some time in our (digital) lives, we’re bound to come across shortened links or URLs, on social networks, for example, you can’t avoid them.
There’s no doubting that they are highly useful. In a tweet, for example, characterized by the famous 140-character limit, a shortened URL creates space to write something else. Moreover, they offer other characteristics, though one of these has become a double-edged sword: You don’t know where it will take you.
This is where you have to tread carefully. A shortened link is really a mystery. You don’t know which website it will take you to or what might appear on the screen. As such, these shortened URLs are the perfect tool for malware and phishing. Click them at your peril.
Yet there’s no need to panic. Just because you come across them every day on Twitter and they could contain a nasty surprise doesn’t mean that every one is a booby trap. Some simple caution and common sense can prevent a catastrophe on your computer.
To start with, be careful with the source of the URL. If it’s an online media channel or blog that is tweeting the headline of an article and a link to it, it is reasonable to suppose that the link will take you to the article. So click away! However, if you find a message from a known (or unknown) contact saying, “Hey, you look great in this photo!” and with a shortened link, be very wary.
Among the numerous services used to shorten inks, some are more reliable than others. The Google and Bit.ly services are among the most secure, though not so much so that you can confidently click them if the source is unknown.
How can you tell if a shortened link is secure?
Using your common sense is a good initial filter to apply when deciding whether or not to click, though it is not infallible. Fortunately, there are quite a few tools that let you expand shortened links, or in other words, see what’s really behind each link and avoid disasters.
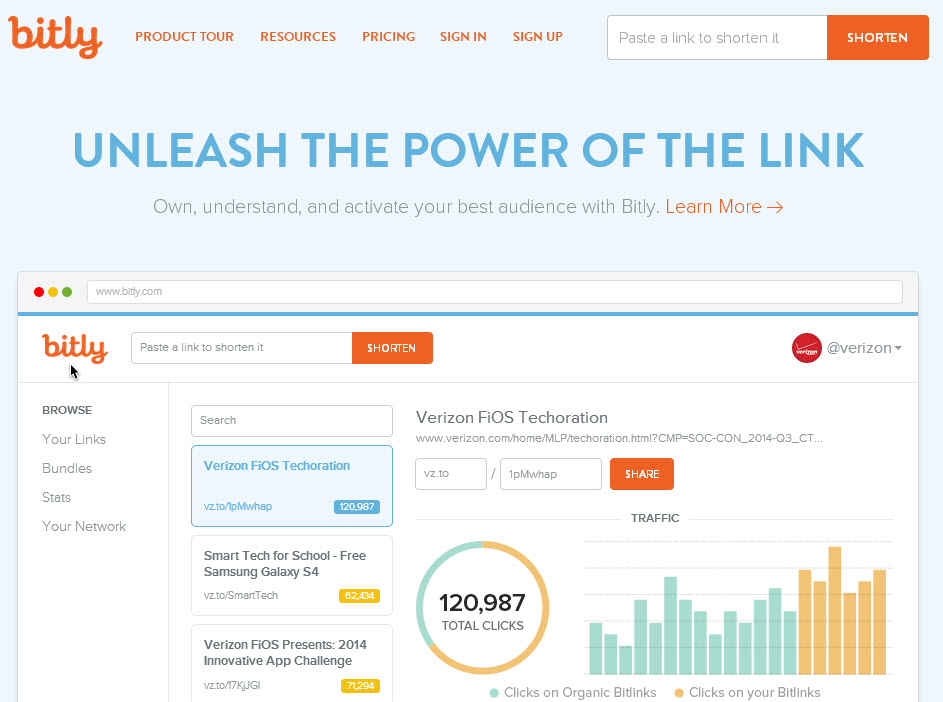
First, here’s a little trick if you come across Bit.ly or Google shortened links. Copy the link, paste it in your browser address bar and, before hitting ‘Enter’, add the “+” symbol. This way you can see the statistics associated with the URL, and more importantly, you can see which website it takes you to, among other things.
Apart from this useful trick, a browser extension or a visit to a certain website could also be enough to prevent any cyber-criminals from giving you a nasty surprise through an apparently interesting link.
Websites such as LongURL or Unshorten.it reverse the process of URL shorteners. Enter any suspect shortened URLs in these pages and you can see exactly where they take you.
As we said before, these are not the only ways of ensuring the security of the shortened URLs that you come across every day on social networks. Probably the most convenient way is to install an extension on your browser that tells you where these links point to without having to continually consult an external website as we described above.
Both for Google Chrome and for Mozilla Firefox, there is a solution to deal with the problem of shortened links.
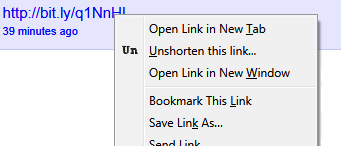
- For Firefox, you can use the corresponding version of Unshorten.it. Whereas the website expands shortened links, the add-on for Firefox does so directly from the browser, thereby saving you a few seconds. Instead of having to open a new tab in the browser and cut and paste the URL, this extension means that you only have to right-click the shortened link and select the option: ‘Unshorten this link’.
- If you use Google Chrome, you also have plenty of options. For example, LongURL (that’s right, the Google browser version of the website we mentioned before), is an add-on that displays all the data regarding the shortened link – including the URL – when you pass the cursor over it.
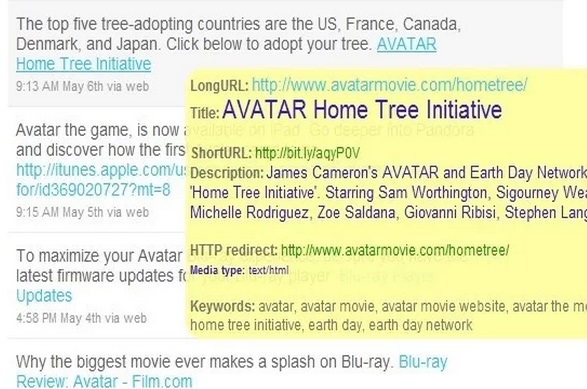
Regardless of the method you choose, you’ll still have to employ some common sense to decide whether the page is bona fide or not. When you expand a link and the name of the website isn’t familiar or what you see is a completely incomprehensible Web address, you’d better be cautious and not go there. In this case, the saying is quite appropriate: ‘Better safe than sorry’.
The post How can you tell if a shortened link is secure? appeared first on MediaCenter Panda Security.