Increasingly, personal and private information is ending up on public view on the Internet. You may not have posted it yourself, you might have just stored it in the cloud, yet some ill-intentioned individual can access and publish it. Photos, videos and other personal data can easily fall into the wrong hands without your permission.
Since last September, more than 100 celebrities have been victims of this type of invasion of privacy. After having uploaded compromising photos to the Apple iCloud, they discovered these images posted on the Web. Someone had accessed and leaked the pictures.
All eyes then turned to Apple. The attack was caused by a security flaw on its mobile devices. A cyber-criminal claimed to have hacked the company’s services to get hold of the images, although the company has rejected this claim on several occasions.
Nevertheless, here we offer six tips to help protect your photos… just in case!
IMAGEN 1C
1. Be careful about what you store in the cloud
If these actresses and models hadn’t uploaded compromising images, it would have been considerably harder for the hackers to get hold of them. Even if you are not a public figure, it’s always a good idea to think about what kind of things you want to store on your phone.
2. Don’t share your account user names or passwords with others
Even though a friend or colleague may have your complete trust, the fewer people who know your credentials, the less chance there is of others finding out. Most online platforms (Facebook, Apple, Google and Yahoo) allow you to boost security with two-factor authentication. If available, it is always a good idea to use it. It basically involves another step in the verification of the user’s identity. This could involve generating a code that the page sends to your phone or another means of contact to verify your identity.
3. Strengthen your passwords to make sure they can’t be guessed by cyber-criminals
One useful tip is for them to contain a mix of numbers, special characters and upper and lower case letters, i.e. make them has complex and varied as possible. The same goes for your Wi-Fi password. It’s also a good idea to change them frequently.
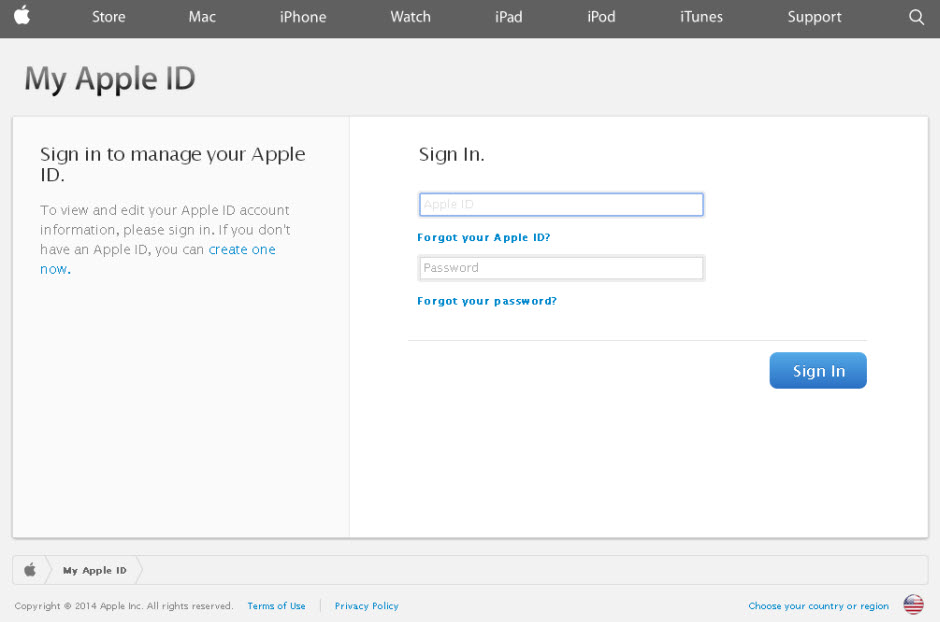
4.  With email, it’s wise to have different addresses for different purposes
Use different accounts for professional, personal or financial affairs. If somebody manages to gain access to one, at least all your data won’t be at risk.
5. Take care with your profile on social networks
Check the privacy options from time to time as sometimes they can be changed or the default settings are re-established without notice. And be careful with what you post online.
6. Use a good antivirus
It will not only keep your computer virus-free but will also identity and help keep Internet fraudsters at bay when, for example, you’re shopping online. Find the antivirus that best meets your needs from out 2015 product lineup.
The post Six tips to make sure your personal photos don’t end up on the Web like those of Jennifer Lawrence appeared first on MediaCenter Panda Security.