ESET’s Ondrej Kubovič: “Worrying about privacy isn’t enough” – here’s how to control your data privacy and online presence.
The post Worrying about data privacy isn’t enough: Here’s how to own your online presence appeared first on WeLiveSecurity
![]()
ESET’s Ondrej Kubovič: “Worrying about privacy isn’t enough” – here’s how to control your data privacy and online presence.
The post Worrying about data privacy isn’t enough: Here’s how to own your online presence appeared first on WeLiveSecurity
![]()
The non-profit organization behind TOR – the largest online anonymity network that allows people to hide their real identity online – has launched an early alpha version of Sandboxed Tor Browser 0.0.2.
Yes, the Tor Project is working on a sandboxed version of the Tor Browser that would isolate the Tor Browser from other processes of the operating system and limit its ability to interact or
![]()
Another blow to the Tor Project: One of the Tor Project’s earliest contributors has decided to quit the project and shut down all of the important Tor nodes under his administration.
Lucky Green was part of the Tor Project before the anonymity network was known as TOR. He probably ran one of the first 5 nodes in the TOR network at its inception and managed special nodes inside the anonymity
![]()
Should be “Shot at sunrise” is the opinion of U.S. politician Michael C.Burgess, the representative for Texas, when talking about the cybercriminals who distribute ransomware that victimizes consumers and businesses.
Ransomware, malicious software designed to block access to a computer system until a sum of money is paid, and the use of exploit kits to distribute it, are adding new challenges to threat detection and protection. And now Angler, an exploit kit, which has been a known Internet threat since 2013, is being used to distribute ransomware. With the sole intent of installing ransomware on victim’s machines.
Our AVG Web Threats team is tracking these widespread ransomware attacks being delivered by the Angler crimeware exploit kit.
The use of exploit kits to distribute ransomware is a new trend – one that could cause widespread ransomware distribution. Exploit kits are software packages readily available for sale and are used by malicious operators to easily create malware that performs a wide variety of malicious functions. The malware is installed on hacked web servers and attacks the machines of visitors to web sites, in many instances, without their knowledge.
There is a common misperception that web users are only at risk if they browse risky sites, however, hacked sites are often brand names and appear safe. Small business sites in particular can be prime targets because they have less security and their visitors typically know the company and trust their brand.
The malware on these sites seeks out vulnerabilities in commonly used tools that improve website experiences, such as Flash, Silverlight and other software that employs Java and PDF-format files. The malware then runs malicious code on the visitors’ machine to install ransomware, backdoors and Spybot clients.
Our AVG Web Threats team has researched a particular instance of a Java exploit commonly found in association with Angler. This threat is detected by AVG, which we’ve been detecting since January. AVG customers who participate in anonymous threat sharing reported 6,123 hacked domains serving Angler in January, 8,260 in February and 4,412 in March.
Angler ransomware installs
TeslaCrypt is the most common type of ransomware installation currently that’s associated with Angler, according to our AVG Web Threats team analysis of this threat. TeslaCrypt encrypts users’ files, including writeable shares, and messages the user to extort payment for recovering the encrypted data. Paying the ransom to unlock files typically does not result in the recovery of the files.
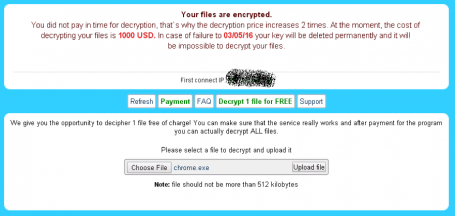
Below are screen shot examples of ransomware attacks that attempt to extort $1,000 USD, payable through the untraceable currency of bitcoins.
Backdoor installs
Our AVG Web Threats team track the Angler-infected host machines have also tracked incidences of downloading malware known as backdoor malcode (commonly Bedep). Backdoor, or Bedep, can snatch passwords and personal confidential data from visitors’ machines.
Protecting your desktop
AVG recommends that consumers and businesses take the following preventive measures:
Protecting web servers
Malicious code from the Angler exploit kit is initially installed on the web pages of vulnerable servers. For businesses, standard security precautions and monitoring are the basic defense. Researchers find a large number of Angler injections on WordPress and Apache servers – these should be given an extra measure of scrutiny.
Our AVG Web Threats team continue to monitor and track threats such as Angler, so that we can deliver the security you need to keep your devices and businesses safe.
![]()
![]()
Alina Simone’s gripping 2015 account of her mother’s extortion ordeal was the first time many non-tech people had heard the term “Ransomware”. It presented a threat that felt intensely personal. It blocked access to data we use to define ourselves: family photos, letters to relatives, tax and financial records, and beloved music and movies.
Flash forward a year, and ransomware is all over the media. The reason for its rise is simple: money.
Before the emergence of ransomware, criminals mainly used (and still use) malware to take control of machines. Malicious code harvested user names, passwords, and credit card numbers. It might have also used infected PCs in a botnet for sending spam or launching attacks that shut down major websites, usually as a decoy while hackers broke in elsewhere.
For Criminals, Ransomware Is Lucrative
Ransomware cuts out the digital middlemen. Rather than collect credit card details that must then be sold on the dark web for a few cents to a few dollars, ransomware demands money directly from the victims. While the amount varies, it tends to be few hundred dollars for individuals.
Yet these small sums are taking a heavy toll. The exact number of ransomware attacks is hard to gauge, as many go unreported. But according to our data they are rising fast. While official complaints about ransomware (and ransoms paid) to the US Department of Justice amounted to only around $24 million in damages in 2015, other numbers are much higher. In April, CNBC estimated the cost of ransomware at around $200 million in the first three months of 2016 alone. Late last year, the Cyber Threat Alliance stated that a single piece of ransomware, CrytopWall v3, resulted in an estimated $325 million in damages worldwide over the course of its lifetime. And as far back as June 2014, the FBI issued a report saying CryptoLocker swindled more than $27 million from users over a two-month period.
Bigger Targets May Mean Bigger Paydays
These numbers speak to the audacity of ransomware purveyors. The long-tail effect of attacking individuals has proven so lucrative, it is unlikely to ever go away. But many organizations also hold sensitive customer data that needs to be protected both to ensure effective service and consumer privacy. That makes them particularly juicy targets to hackers.
Healthcare provides are a case in point. If they lose control of patient information, they may be unable to deliver treatment when needed. There are also strict legal requirements governing the protection of patient data. Both make them subject to lawsuits that could cost them far more than what they would have to pay in ransom. A hospital in Hollywood, California, paid $17,000 in bitcoin to hackers after being locked out of their data. Fortunately, so far, other reported attacks have fared less well. Healthcare providers in Kentucky and Ottawa refused to pay, as no patient data was compromised; and an attack in Germany was quickly contained by fast-acting IT staff.
Still, the hospitals have had to invest considerable time and resources into fighting the attacks. They will also need to launch multiple efforts internally and externally to restore patient trust.
And hospitals are not alone. A 2016 report by the Institute for Critical Infrastructure Technology, an industry think tank, declares 2016 the year of ransomware, suggesting few organizations are safe. For instance, systems at an Israeli electrical utility were infected by ransomware after a phishing attack. A utility in Michigan has been allegedly attacked. Multiple police stations have been hit and paid ransoms to regain access to their systems. Local governments are increasingly feeling the pressure, with attacks reported in places as diverse as Alto City, Texas, and Lincolnshire, UK. And criminals have subverted online adverts of venerable media organizations, such as the BBC and NYT, turning their websites into potential sources of drive-by ransomware.
The Right Protection Saves Money
This is why protection is essential, especially for individual users, most of whom lack the expertise and resources of even modest city councils and small hospitals. Over a three-month period earlier this year, a conservative estimate by AVG is that its antivirus prevented around $47 million in extortion demands through the interception of just three types of ransomware: Cryt0L0cker, CryptoWall, and TeslaCrypt. And that number says nothing of the mental and emotional costs that would have resulted from feeling violated or the costs of replacing machines, software, and media if a victim decided not to pay.
AVG does not recommend paying. There is no guarantee criminals will release the files. They may also leave a piece of malicious code behind that allows them to strike again. It is better to call tech support, salvage what you can, make frequent backups, and build a fortress around your PC – and thus prevent the writing of another news story like Alina Simone’s.
![]()
![]()
“Talent has no Age Limit”
That’s what I said for a 10-year-old Finnish boy on our official Facebook page while sharing his recent achievement with our readers i.e. Winning $10,000 bug bounty from Instagram.
Last Tuesday when we at The Hacker News first acknowledged this talented boy and the flaw he discovered in image-sharing social network Instagram, I did not have an idea that the Facebook
![]()
Spring is here! The sun is shining, winter clothes are pushed to the back of the closet, and people are heading to the beaches and parks to embrace spring weather. Well, at least here in California.
For many of us, we view spring as a time to purge and clean – out with the old and in with the new – a new opportunity to throw out old clothes or to make the garden look a little tidier. So why not clean up your digital life as well?
Your phone may not be the first thing you think of when you think of Spring Cleaning but if your phone is like mine, then your entire life is on it! Looking at my photos alone, I have 944 pictures. Many of them are duplicates, as I always take more than one to make sure I get a good one and then I forget to delete them later. If I go through them one-by-one it will be time consuming, not to mention that I’ll probably get distracted by messages and other notifications.
That why I recommend you install AVG Cleaner™ for Android™ from the Google play store. It has a great photo cleaning app that identifies “bad” photos and allows you to review them the way you could review photos in some dating apps, swipe right to keep or left to reject. It also shows duplicate photos and makes automatic recommendations.
Because photos contain a lot of data, it’s also a good time to review the settings on your phone to ensure that you don’t fall foul of publishing your location when you did not mean to. Here are a couple things to keep in mind:
– Photos can contain specific location information stored in metadata within the image itself.
– The location data usually includes the precise GPS coordinates of where the photo was taken, as well as the time and date it was captured.
It’s an easy task to switch off the feature that allows location data to be stored in the photo. Here are the steps:
In addition to cleaning out photos, AVG Cleaner™ for Android™ also identifies apps and games that you don’t use, which allows you to delete them to save valuable space. It also contains tools that give you data on which apps use the most storage, battery and data – all so you can make the decision whether to keep them. In my phone, I deleted 13 apps; including a parking payment apps in cities where I visited one time and apps I downloaded once just to see what they do.
And of course, I can’t write a blog about cleaning up your phone without mentioning updating your antivirus. If you have AVG AntiVirus for Android™, open it up to run a scan for viruses. If you don’t have the app, you can always download it here.
Not only does cleaning your phone make the phone perform better but it’s like new again! Mine is ready for the next round of stuff that I am going to load on it. All I need is a new screen protector!
To learn more about me and receive the latest news from AVG:
Follow me on Twitter @TonyatAVG
Follow AVG on Twitter @AVGFree
![]()
![]()
In Brief
What if we could Predict when a cyber attack is going to occur before it actually happens and prevent it? Isn’t it revolutionary idea for Internet Security?
Security researchers at MIT have developed a new Artificial Intelligence-based cyber security platform, called ‘AI2,’ which has the ability to predict, detect, and stop 85% of Cyber Attacks with high accuracy.
Cyber security
![]()
In Brief
Chrome apps and extensions make things easier, but they can also do terrible things like spy on web users and collect their personal data.
But, now Google has updated its browser’s User Data Policy requiring all Chrome extension and app developers to disclose what data they collect.
Furthermore, developers are prohibited from collecting unnecessary browsing data and must also use
![]()
Two Google engineers have developed a draft version of an API called WebUSB that would allow you to connect your USB devices to the Web safely and securely, bypassing the need for native drivers.
WebUSB – developed by Reilly Grant and Ken Rockot – has been introduced to the World Wide Web Consortium’s Web Incubator Community Group (W3C WICG), is build to offer a universal platform that could
![]()