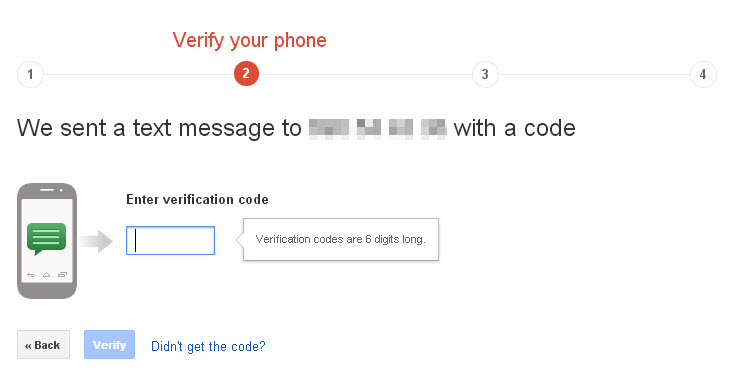
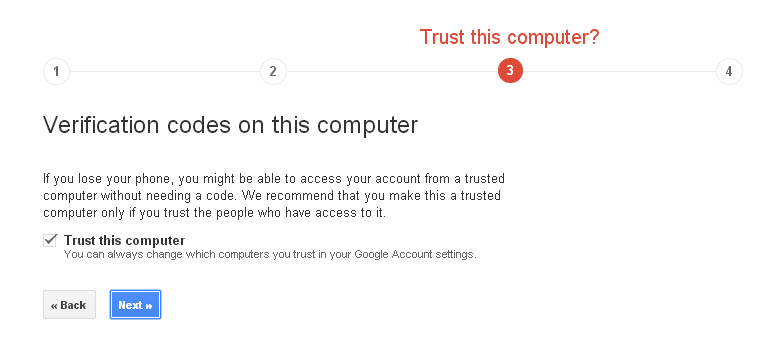
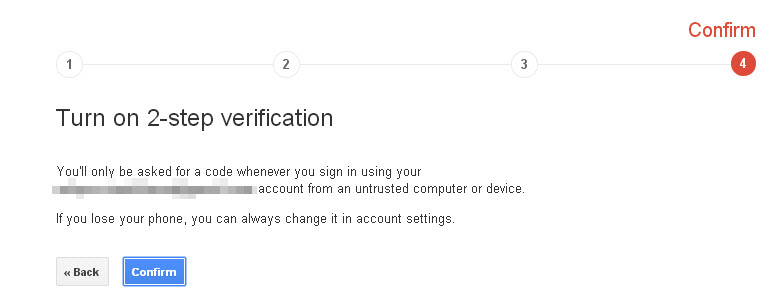
A few precautions can make a huge difference in the safety of your phone and the important things you saved on it.

Follow our tips to secure your phone and the data on it.
We talk a lot about protection and privacy here in our blog. It’s a bit obvious as our “life” is in our devices nowadays: Photos of our last trip or our loved ones, videos of our children playing and growing up, contacts both professional and personal. All our precious and irreplaceable data is stored in these little machines. Take a minute of your time and follow us in this easy tour to protect them and save a lot of time and headaches.
1. Set your lockscreen
You wouldn’t leave your home door unlocked, would you? Same goes for your phone with all your private data. Set a password or PIN to prevent direct and easy access to your phone. Gestures and face recognition are less secure, but are better than nothing.
2. Hide your passwords from nosy people
You will argue that people around you can look over your shoulder and see what PIN or password you’re typing or gesture you make. Generally, we’re not worried about trustworthy people around us, but what about strangers in a public place like a bus or train? Open your phone settings and hide your passwords by unchecking the option: Settings > Security > Make passwords visible.
3. Protect your apps with a PIN
Not all apps are equal when it comes to security and privacy. Probably the weather app or calculator won’t keep your personal info. However, your messages and banking apps will thank you if you help them to keep their data private. You can imagine what might happen if your kids to open a specific app while they’re playing in your devices. Use Avast Mobile Security to set a PIN to block access to your apps. As an extra security measure, it will be good that your lockscreen and Avast PINs are different ones.
4. Disable installation of apps from unknown sources
If you do not use other app stores besides Google Play, then uncheck the option “Unknown sources” in your phone’s Security Settings page. Even the Google Play Store sometimes allows malware to get by. It’s well known that most Android malware are fake apps disguised as legitimate apps, so double check the publisher. Be cautious of downloading from fake sites disguised as official ones – check the URL. Avoid completely pirated and cracked sources.
5. Set Avast Mobile Security to scan any app before installing
If you really need to use legal third party stores, like Amazon or F-Droid, please be careful: Keep Avast Mobile Security always on. You know that Avast scans any installed and running app. But do you know that you can set it to scan any app that is about to be installed? After you’ve installed Avast, when you’re about to install a new app, the phone will ask you if you want Avast or the default installer to handle the installation by default. Use Avast, it will scan and then release the app to the default installation process.
6. Disable USB Debugging
This tip is for advanced users. If you have enabled Developer options into your device (and you will know exactly if you did as you’re an advanced user!), please, turn USB debugging off. You will protect your device from outside abuse (via adb connections) if you do so. You don’t need it to be on all the time.
7. Install and set Avast Anti-Theft
This is an old tip, but it’s so important that it should be on all smartphone safety tips lists. Just note that installing is not enough. You need to properly configure Avast Anti-Theft (don’t worry, there is an easy wizard for it) step-by-step. It’s good to check if your location services are properly set also, otherwise, it will be difficult to track it. In other words, go to Settings > Location Access and set High accuracy mode.
We’ll talk about the other 7 tips in next days, so come back to the Avast blog.










 Many of us now prefer to shop online: you can avoid the queues, it’s easier to compare goods and prices…
Many of us now prefer to shop online: you can avoid the queues, it’s easier to compare goods and prices…