Read the headlines and you would think cyber-crime was all about big brands fighting to keep customer data out of hackers’ hands.
You might even think it is about governments and cyber-espionage.
But behind the headlines, there is a day-to-day story of small business under attack.
So to mark National Cyber Security Awareness Month, we’re working with the National Federation of Independent Business (NFIB) to share free tools and resources and about online threats.
Through October, we’ll help NFIB members and small business owners learn more about some of the practical issues around cybersecurity.
We’ll share information about the common tricks and tactics of hackers, and we’ll explore the issues around Bring Your Own Device (BYOD) and the challenge of keeping a business secure when the lines are blurring between an employee’s personal tech and their professional life.
This week we’re encouraging small business owners and NFIB members to take our AVG Small Business IT Security Health Check.
It’s a simple free tool to help business owners think about how well-prepared they are against cyber threats.
The tool poses 17 multiple choice questions across a range of security topics: from password security to IT infrastructure.
There are also questions about what plans business owners have in place to deal with the fall-out if a security breach happens and customer, employee or suppliers’ personal information is compromised.
In the weeks ahead, we’ll share updated versions of our free ebooks through the NFIB’s regular email newsletter to members:
- Digital Policy Guide
What kind of issues emerge from employees and business owners using social media for personal and professional life? This guide looks at how social media can be a positive tool for businesses – and a management challenge if it’s misused. Download the guide.
- Hackers and Hacking
What are hackers looking for and what are their common tricks and tactics? Employees’ payroll data? Customer and suppliers’ bank details? This guide covers the threat of hacking, the motives behind it, what is at risk and how to combat these kinds of attacks. Read the ebook.
- Bring Your Own Device
Mobile tech from smartphones to tablets means that employees can keep in touch with friends and family on the same device they use to keep track of work emails, appointments and data. So what does that mean for your business? This guide looks at the issues around BYOD.
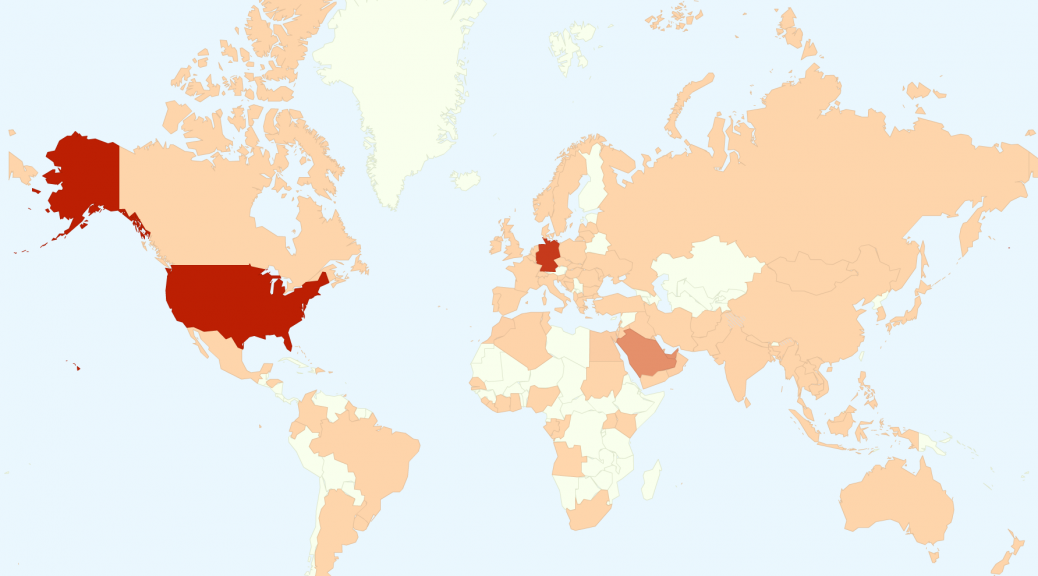
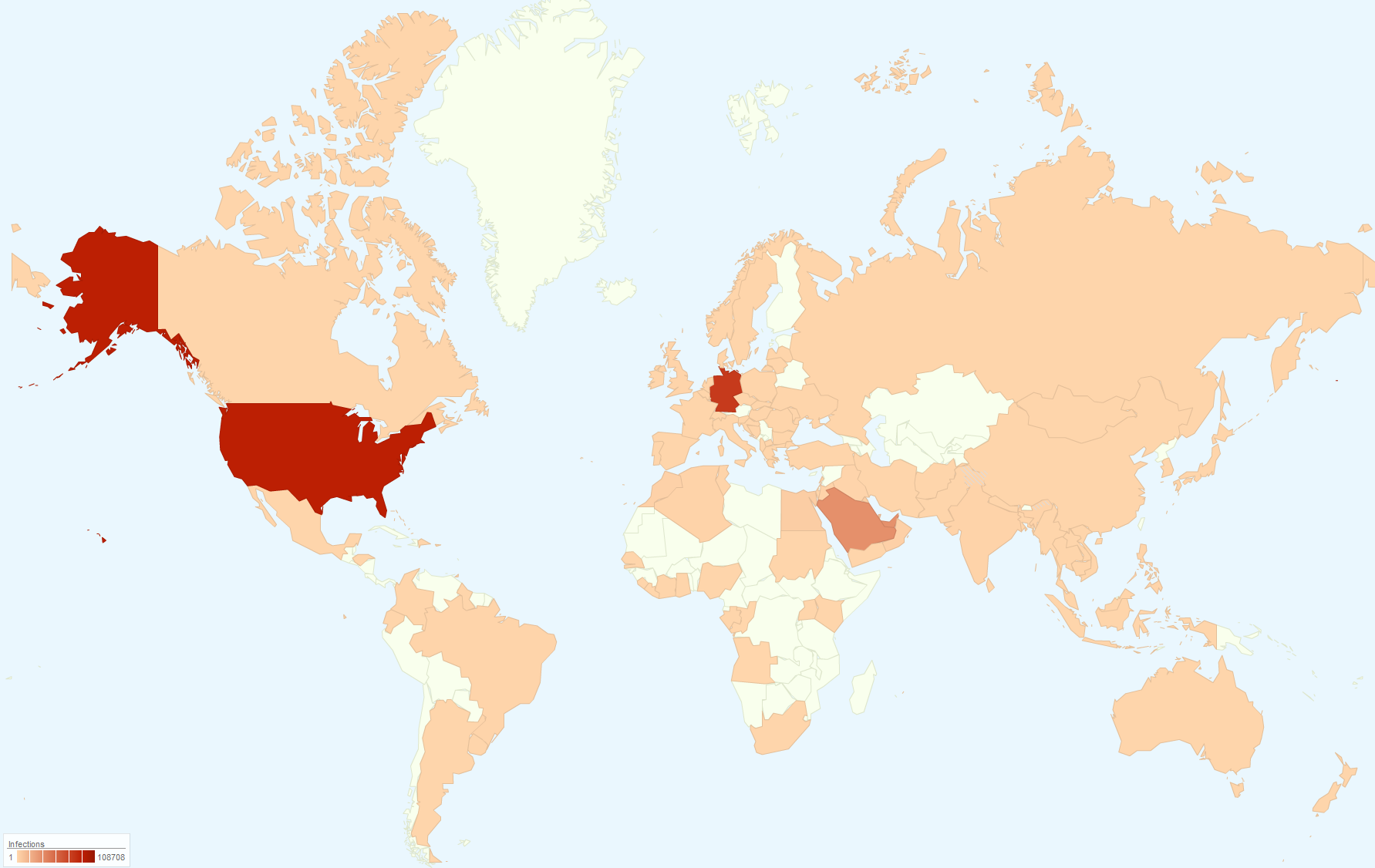
Sadly, there’s no way to stop hackers from trying to breach the virtual defences of small businesses. Wherever they are in the world, hackers will keep trying to find valuable data and disrupt business operations. And as Steve Chabot (R-OH), Chairman of the Congressional Small Business Committee, explained earlier this year, 71 percent of cyber-attacks are targeted at businesses with fewer than 100 employees.
So we hope our association with the NFIB will spread awareness of the issues and help small business owners feel better prepared to deal with online threats and ready to take steps to make their businesses more secure in future.
![]()
![]()