A dozen vulnerabilities, including three critical architectural issues, in PeopleSoft implementations were discussed this week at Hack in the Box, putting ERP security in the spotlight.
Tag Archives: passwords
Do Millennials Suck When It Comes To Security?
Millennials (or Generation Y) are those who were born from the early 1980s to the early 2000s. A study now looked at the impact which generational attitudes have toward security issues and compared Millennials Generation X/Gen X (those born between 1965 and 1980) and the “baby boomers” (born between 1946 and 1964).
You would normally think that the Millennials know what they are doing when it comes to technology, considering that most of them grew up with it. But while it is a big plus when it comes to handling devices and navigating around the net, the sense of well-being also seems to be their Achilles heel and leads them to being more careless with privacy concerns and a few other security aspects. The study backs this up with some key findings:
- “Millennials have the worst password reuse habits of all demographics: 85 percent admit to re-using credentials across sites and services.
- Risky behavior can be found across demographics: 16 percent of millennials and 14 percent of Gen-Xers accept social media invites from strangers “most of the time.”
- Millennials are most likely to find security workarounds: A combined 56 percent admit they would “very” or “moderately likely” evade restrictive workplace controls. “
On the other hand, the paper also shows that the other included generations show risky behavior as well (though not in the same areas: Baby Boomers for example may pose a rather big BYOD risk; 48% use personal devices to access work related content).
Nonetheless it would seem that Millennials are easy prey for hackers: Reusing passwords and being too trusting on social media (which may or may not lead you to fall victim to social engineering) can lead to unwelcome results.
The post Do Millennials Suck When It Comes To Security? appeared first on Avira Blog.
Security Questions Not So Secure
The Internet knows a lot about you, including your mother’s maiden name, your favorite food, and what street your first pet grew up on. And, according to some new research from Google, attackers have a good chance of figuring those things out pretty easily, too. The security questions that Google and other companies ask users as […]
Hackers Using Starbucks Gift Cards to steal money
Earlier in May, researcher Bob Sullivan reported that hackers were targeting Starbucks mobile users and using the Starbucks app to steal money through linked credit cards.
The Starbucks app links to a credit card so that the user can prepay for goods and purchase Starbucks gift cards for friends and family to spend in store.
Reports indicate that the gift cards are fundamental to the attacks.
After gaining access to the victim’s Starbucks account, attackers create a new gift card for the entire balance of the account and issue it to themselves. The problem is then compounded as the Starbucks app automatically tops up the user’s balance when it gets low. This means that the attacker can then strike again.
Within a few minutes, attackers could potentially siphon hundreds of dollars through gift cards without even needing the victim’s credit card details.
In a recent blog post, Starbucks recently defended the security of their app and said that “News reports that the Starbucks mobile app has been hacked are false.”
Instead, they say that it is reusing login details from other sites that is putting customers at risk:
Occasionally, Starbucks receives reports from customers of unauthorized activity on their online account. This is primarily caused when criminals obtain reused names and passwords from other sites and attempt to apply that information to Starbucks. To protect their security, customers are encouraged to use different user names and passwords for different sites, especially those that keep financial information.
This isn’t the first time that the Starbucks app has come under fire, after last year it emerged that it stores users’ passwords on the device in plain text.
How to help protect yourself from attacks such as these:
Pick a strong, unique password
It goes without saying that this attack would not be possible if hackers were shut out of Starbucks accounts. Therefore, keeping a strong and unique password (one that is not used on any other site) is one of the most important things you can do to help protect yourself from an attack like this. For help creating a strong password, check out this simple guide.
Turn off or limit auto-top up
One of the things that makes this attack so dangerous is the fact that the damage can escalate rapidly thanks to the auto top-up functionality used by the Starbucks app (and many others like it).
While automatically replenishing your account balance can be an incredibly convenient thing, if you are concerned about attacks like these, disable or set a deposit limit on your auto top-up.
Regularly check your accounts
Just like with online banking fraud, one of the best ways to protect yourself or recover from attacks such as this is to stay vigilant. Regularly check your bank statements and online account histories for suspicious activity and do not hesitate to get in touch with your bank or retailer should something unexpected appear.
For Starbucks users, if you see any suspicious activity on your Starbucks Card or mobile app, please immediately notify Starbucks customer service at 1-800-STARBUC.
![]()
![]()
Technology mistakes to stop making today
We love our fans and followers on Twitter because they frequently alert us to great resources. It happened today when we received a tweet from @LoveNerds4Ever letting us know that Avast Antivirus was mentioned on a Sacramento (California) News10 video segment. Thanks, Shawna!
@avast_antivirus You were mentioned! “Tech Mistakes” Ryan Eldridge #NerdsOnCallComputerRepair on #News10Sacramento https://t.co/pFAdSIN0N2
— Shawna M. Bell (@LoveNerds4Ever) May 14, 2015
The guest on this video segment is Ryan Eldridge, co-founder of Nerds on Call, a computer repair Business in Sacramento. He spoke to reporter Keba Arnold about technology mistakes that people typically make. These simple, but oh, so important points, are ones that we continually try to make, and Ryan puts it all together in one good video. Watch it now.
The security recommendations that Ryan makes:
- Run updates on your computer and mobile phone. Program updates and security patches are very important to keep your device up to date and running optimally.
- Download apps and programs from places you know and trust. On your mobile phone this would be the Google Play Store or Amazon App Store. For your computer, he says it’s a little bit harder, but suggest that you visit download.com, CNET’s well-known download site where you can read user reviews and see the reputation of the app before you download.
- Ryan reminds computer users that when they get a new device antivirus software may be pre-installed, but it is a trial for a limited time. After it expires, you need to get protected with a quality antivirus product. Ryan recommends Avast Free Antivirus for your computer, your Mac, and your mobile phone.
- Ms. Arnold confesses that she has one email address that acts as a catch-all for everything. Ryan says this is a no-no because if a hacker breaks into that email address, then he has access to everything. Ryan suggests that you have separate email addresses for friends and family, work, one for shopping, and one for banking.
- Passwords, admittedly are a pain in the you-know-what. Ryan suggests using an algorithm, or a kind of personal code, to construct your own passwords. For example, you can use a line from your favorite song, say Somewhere Over the Rainbow. Use the first letter of each word, use letters from the website name, and end with a series of numbers. Each password will be unique and known only to you.
And Ryan, we have a tip for you! Small businesses like yours need security protection too, and consumer antivirus like Avast Free Antivirus, doesn’t do the trick when you need to manage multiple devices, platforms, and people in remote locations. Adding to our collection of free products is the new Avast for Business. Avast for Business is free to use for as long as you want and for an unlimited number of admins and devices.
Unpredictability is key in password strength
The latest report from infosec provider Praetorian suggests that when it comes to hacking a password, the sequence and consistency of the characters is just as important as the actual strength of the password itself.
Using a technique called a mask attack, attackers break a password down into their component elements such as upper case letters (u), lower case letters (l), digits (d) and symbols (s).
In their example, Praetorian used “Password1234” which when viewed in this system becomes “ullllllldddd”. This string of letters is known as a mask. Each letter in the chain denotes the character type (u= upper case).
Using this technique, Praetorian analysed nearly 35 million leaked passwords from various sources. What they found was surprising.
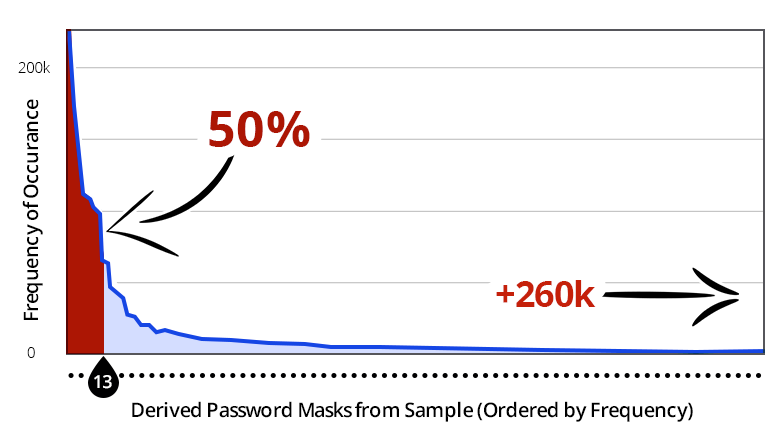
Of the 35 million analysed passwords, half of used the same 13 masks. This means that despite the millions of variants of characters, digits and symbols, in our passwords, as many as half of us are using a very limited selection of masks.
Naturally our predisposition for these certain masks makes our passwords much easier to hack. Not to mention that many people also use dictionary words and personally identifiable information in their passwords.
Why do we behave like this?
Praetorian posits that our preference masks is down to the way that we are informed to create strong passwords. A simple example of this would be to use a capital letter in the password. Conventional behavior leads us to use it at the start of a password and use symbols such as ‘!’ at the end.
How to improve your password safety.
The most important thing to do to help make your passwords more difficult to crack is to use an unusual mask. Don’t be tempted to start your password with a capital and insert your symbols and digits somewhere other than the end.
Password managers can also help you generate strong, long and random passwords that use a wide variety of masks.
![]()
![]()
Google Releases Password Alert Extension for Chrome
Google is rolling out a new extension for Chrome that will monitor users’ logins and warn them if they enter a Google password on a non-Google page, a move designed to help protect users against phishing attacks. The new extension, called Password Alert, works for both consumer accounts and Google Apps for Work accounts. Company […]
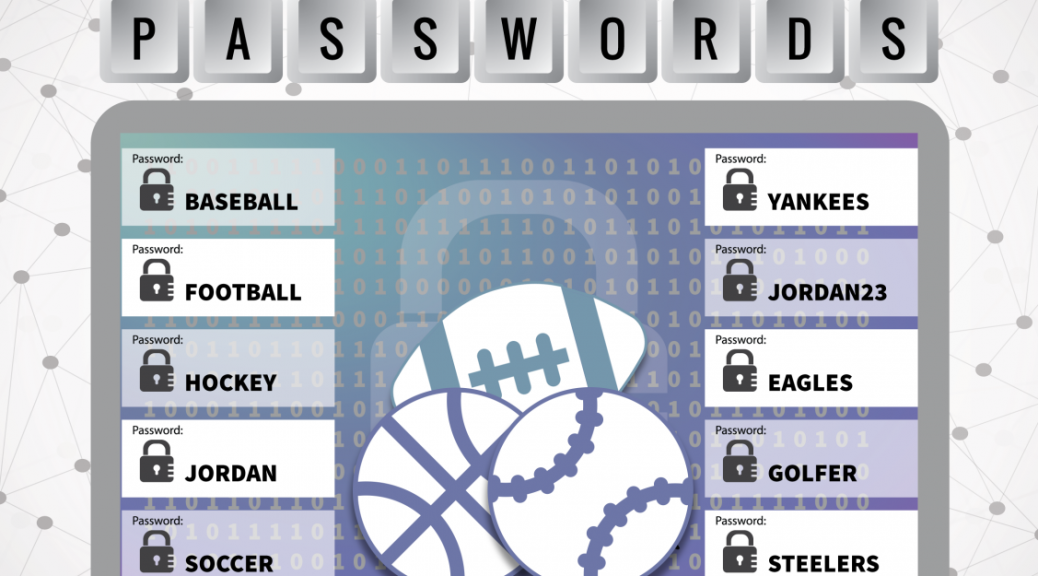
Sports fans, avoid these weak passwords!
Earlier this week, a list of 25 worst sporting passwords was released by SplashData, and includes a whole raft of easily guessable passwords, the most common being “baseball” and “football”.

In fact, baseball and football are so common that they appeared on the list of overall worst passwords published earlier in 2015.
It goes without saying that if you see your password among this list it really is time to change it. Having a weak password can make it easy for attackers or scammers to gain access to your accounts and the data stored within.
How to create a strong password:
Creating a strong password is much easier than winning the World Series and in a few simple steps you can have a password that can help keep your data secure while also being easy to remember.
For tips on what to avoid when getting a new password, be sure to check out this video from AVG Security Expert Michael McKinnon.
ESET’s Mark James on addressing business security employee issues
ESET’s Mark James on the issues employees have with business security measures, and how to counter the difficulties without compromising safety.
The post ESET’s Mark James on addressing business security employee issues appeared first on We Live Security.
Banking Trojan Vawtrak: Harvesting Passwords Worldwide
Over the last few months, AVG has tracked the rapid spread of a banking Trojan known as Vawtrak (aka Neverquest or Snifula).
Once it has infected a system, Vawtrak gains access to bank accounts visited by the victim. Furthermore, Vawtrak uses the infamous Pony module for stealing a wide range of login credentials.
While Vawtrak Trojans are not new, this particular sample is of great interest.
How and where is it spreading?
The Vawtrak Trojkan spreads in three main ways:
- Drive-by download – in the form of spam email attachments or links to compromised sites
- Malware downloader – such as Zemot or Chaintor
- Exploit kit – such as Angler
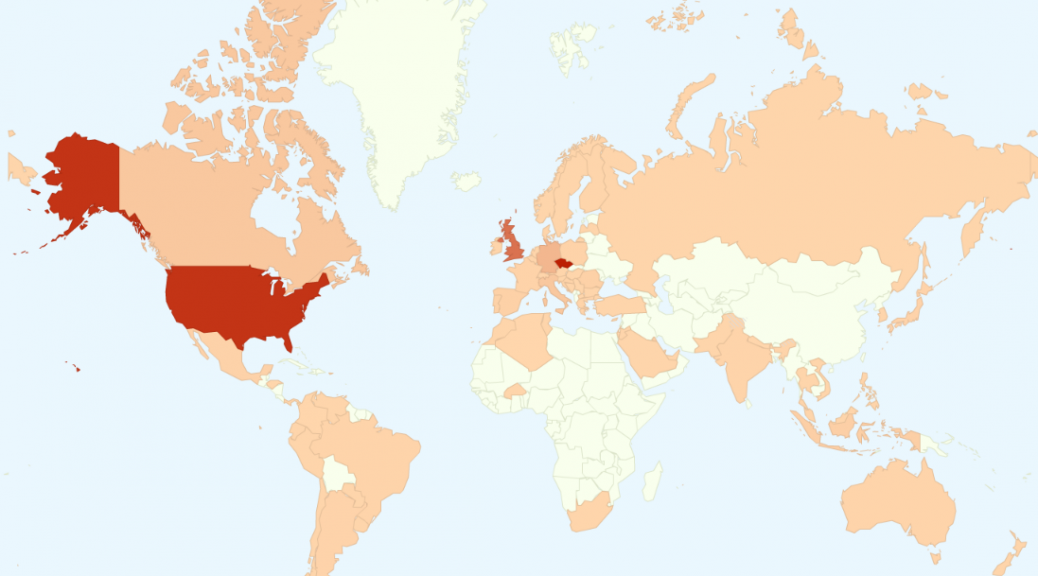
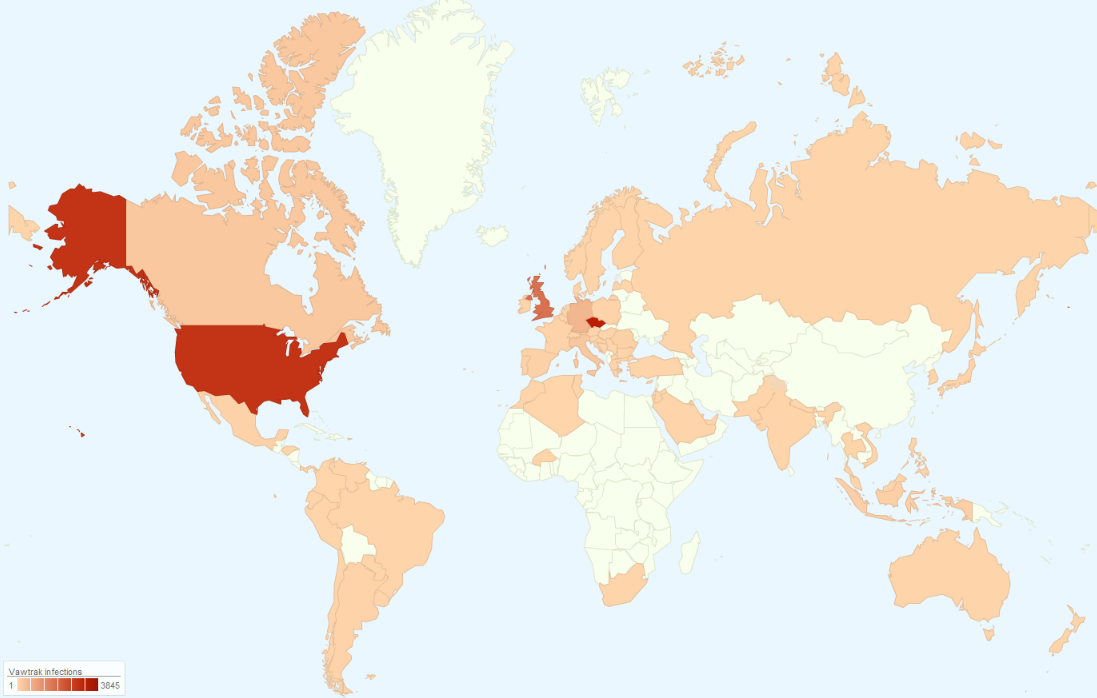
Based on our statistics, the Czech Republic, USA, UK, and Germany are the most affected countries by the Vawtrak campaigns this year.
What are the features of this Vawtrak?
This Vawtrak sample is remarkable for the high number of functions that it can execute on a victim’s machine. These include:
- Theft of multiple types of passwords used by user online or stored on a local machine;
- Injection of custom code in a user-displayed web pages (this is mostly related to online banking);
- Surveillance of the user (key logging, taking screenshots, capturing video);
- Creating a remote access to a user’s machine (VNC, SOCKS);
- Automatic updating.
Of particular interest from a security standpoint is that by using Tor2web proxy, it can access update servers that are hosted on the Tor hidden web services without installing specialist software such as Torbrowser.
Moreover, the communication with the remote server is done over SSL, which adds further encryption.
This Vawtrak sample also uses steganography to hide update files inside of favicons so that downloading them does not seem suspicious. Each favicon is only few kilobytes in size, but it is enough to carry a digitally signed update file hidden inside.
Detailed analysis
Our complete analysis of this malware is too long to publish in full on this blog so we have prepared a detailed white paper that describes this infection, its internals and functions in detail.
You can also download the report here
Stay Safe
While this Vawtrak Trojan is very flexible in functionality, it’s coding is mostly basic and can be defended against. At AVG, we protect our users from Vawtrak in several ways:
- AVG LinkScanner and Online Shield provide real-time scanning of clicked links and web pages containing malicious code.
- AVG Antivirus for generic detection of malicious files and regular scans.
- AVG Identity Protection, that uses a behavioral-based detection, will detect even the latest versions of such infections.
- AVG Firewall prevents any unsolicited network traffic, such as communication with a C&C server.