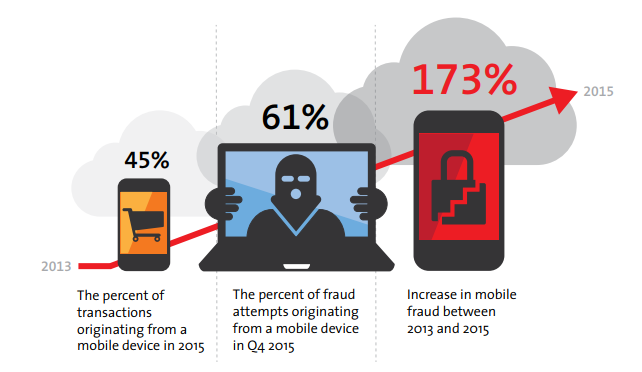
In a recent study by Panda Security in collaboration with Nielsen, 91% of Spanish SMEs confirmed that they were victims of daily IT attacks. The viruses that wreaked havoc on their systems included Trojans (33%) and spyware (25%). The viruses entered the company systems from unsecure websites (39%), downloaded programs (23%), and email malware (19%).
It is fundamental for both small and medium-sized companies to allocate resources for security and establish security policies, otherwise the losses can be substantial and costly. The losses can include anything from information theft to a temporal IT collapse.
Here are some of the most basic, yet crucial, cybersecurity tips for SMEs:
Protect Your Office
Of course the easiest way to directly attack a company’s systems is by having physical access to the IT equipment. Companies should control who enters facilities with identification cards or some kind of biometric identification. Pay special attention to external personnel (cleaning services, external companies, etc.) and visitors, and make sure that they identify themselves properly. Alarms and video surveillance systems are other great ideas.
Secure Passwords
As a rule of thumb, all of your employees should use passwords that mix capital and lowercase letters, numbers and symbols, and should refrain from using personal information, etc. It is also important that they change passwords frequently, at least once every six months.
Keep Your Software Up-to-Date
In respect to downloading and running programs on company computers, there is an easy rule to follow: if you don’t need it, don’t install it; if you need it and you install it, keep it updated; if you stop using it, uninstall it. If you follow these rules you will save yourself from a lot of headaches.
Don’t let Your Employees Download Pirated Software
As we explained earlier, pirated copies of programs are common entry points for malware. In order to keep these unlicensed programs from threatening your company, it is important to establish an adequate software management policy. This includes keeping an updated inventory, controlling program licenses, and educating your employees.
Be Careful with USBs
Be aware of all external devices that connect to your company’s devices, whether they are external hard drives, memory cards, or anything else that could poke holes into your system and threaten sensitive data. To avoid problems, provide your employees with secured pen drives (the kind that encrypt information and are password protected) and define what information can be transferred using this type of device or should be sent by other means. Likewise, make sure that all appropriate files that come from external devices are tested with an antivirus before they are copied or run on company computers.
Back-up Your Data
Ransomware has grown to be the largest threat to companies. If you want to keep valuable information safe during a cyber-attack, backing-up your files and information is fundamental. We recommend that you keep two backups: one stored on the cloud and another physical copy (an external hard drive, pen drive, etc.).
Invest in Hardware
There are several inexpensive devices that are easy-to-use and will help improve the security in your systems. Some of this hardware includes security cables for laptops, U2F keys, accessories for securely charging up your mobile device in public hot spots. Setting aside sufficient capital for security hardware can save your business money in the long run.

Educate Your Employees
The weakest link in your company’s security chain is the people. Training and educating your workforce should be a priority. That alone could save you from fraud and vulnerabilities that begin with phishing and social engineering.
Their Vulnerabilities Are Your Vulnerabilities
Employees may be the weakest link, however, businesses that provide products and services for your company are an even bigger threat. It is important to legally protect yourself from the vulnerabilities that one of these suppliers may have and carry out inspections periodically, in order to ensure that all related businesses respect good security practices.
Install an Antivirus
When using computers or mobile devices, before they are connected to the internet you need to install a good antivirus. This measure is fundamentally important at both home and at work. A cybersecurity solution for businesses will protect your organization’s devices and information in all types of circumstances, even when employees are careless or make errors.
The post Ten Steps That Will Guarantee Cybersecurity in Your Business appeared first on Panda Security Mediacenter.
![]()