Academics studying 283 Android VPN apps quantified a number of problems associated with native platform support for VPN clients through the BIND_VPN_SERVICE.
Tag Archives: IPv6
Juniper Hotfixes Shut Down IPv6 DDoS Vulnerability
Juniper Networks announced patches for a serious vulnerability in the handling of IPv6 packets that is says could leave its Junos OS and JUNOSe routers open to a distributed denial of service (DDoS) attack.
FreeBSD Patches Kernel Panic Vulnerability
FreeBSD has patched a kernel panic vulnerability is versions compiled to support IPv6 and SCTP.
Not using IPv6? Are you sure?
Internet Protocol version 6 (IPv6) has been around for many years and was first supported in Red Hat Enterprise Linux 6 in 2010. Designed to provide, among other things, additional address space on the ever-growing Internet, IPv6 has only recently become a priority for ISPs and businesses.
On February 3, 2011, ICANN announced that the available pool of unallocated IPv4 addresses had been completely emptied and urged network operators and server owners to implement IPv6 if they had not already done so. Unfortunately, many networks still do not support IPv6 and many system and network administrators don’t understand the security risks associated with not having some sort of IPv6 control within their networks setup even if IPv6 is not supported. The common thought of not having to worry about IPv6 since it’s not supported on a network is a false one.
The Threat
On many operating systems, Red Hat Enterprise Linux and Fedora included, IPv6 is preferred over IPv4. A DNS lookup will search first for an IPv6 address and then an IPv4 address. A system requesting a DHCP allocation will, by default, attempt to obtain both addresses as well. When a network does not support IPv6 it leaves open the possibility of rouge IPv6 DHCP and DNS servers coming online to redirect traffic either around current network restrictions or through a specific choke point where traffic can be inspected or both. Basically, if you aren’t offering up IPv6 within your network someone else could.
Just like on an IPv4 network, monitoring IPv6 on the internal network is crucial for security, especially if you don’t have IPv6 rolled out. Without proper monitoring, an attacker, or poorly configured server, could start providing a path way out of your network, bypassing all established safety mechanisms to keep your data under control.
Implementing IPv6
There are several methods for protecting systems and networks from attacks revolving around IPv6. The simplest, and most preferred method, is to simply start using IPv6. It becomes much more difficult for rouge DNS and DHCP servers to be implemented on a functioning IPv6 network. Implementing IPv6 isn’t particularly difficult either.
Unfortunately IPv6 isn’t all the simple to implement either. As UNC‘s Dr. Joni Julian spoke about in her SouthEast LinuxFest presentation on IPv6 Security, many of the tools administrators use to manage network connections have been rewritten, and thus renamed, to support IPv6. This adds to the confusion when other tools, such as iptables, require different rules to be written to support IPv6. Carnegie Mellon University’s CERT addresses many different facets of implementing IPv6 including ip6tables rules. There are many resources available to help system and network administrators setup IPv6 on their systems and networks and by doing so networks will automatically be available to IPv6-only networks of the future present.
Blocking and Disabling IPv6
If setting up IPv6 isn’t possible the next best thing is disabling, blocking, and monitoring for IPv6 on the network. This means disabling IPv6 in the network stack and blocking IPv6 in ip6tables.
# Set DROP as default policy to INPUT, OUTPUT, and FORWARD chains. ip6tables -P INPUT DROP ip6tables -P OUTPUT DROP ip6tables -P FORWARD DROP# Set DROP as a rule to INPUT and OUTPUT chains.ip6tables -I INPUT -p all -j DROP ip6tables -I OUTPUT -p all -j DROP
Because it can never known that every system on a network will be properly locked down, monitoring for IPv6 packets on the network is important. Many IDSs can be configured to alert on such activity but configuration is key.
A few final words
IPv6 doesn’t have to be scary but if you want to maintain a secure network a certain amount of respect is required. With proper monitoring IPv6 can be an easily manageable “threat”. Of course the best way to mitigate the risks is to embrace IPv6. Rolling it out and using it prevents many of the risks already discussed and it could already be an availability issue if serving up information over the Internet is important.
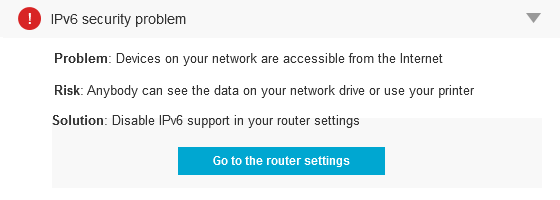
How to disable IPv6 support in your router settings
After the previous articles you should be convinced that router vulnerabilities are one of the major concerns in network security. As you already know, the new Avast 2015 version includes a security feature called Home Network Security (HNS) which scans your network and router for vulnerabilities and prevent threats.
One serious problem occurs when when IPv6 (Internet Protocol version 6) is enabled (both by the ISP and on the router), but there is no IPv6 firewall being used. Which means that anyone on the Internet can access devices on the network (like printers, network disks, etc.). This is often the case because the routers are small, embedded devices that cannot handle IPv6 firewalling.
The main advantage of IPv6 over IPv4 is its larger address space: it allows 2128 or approximately 3.4×1038 addresses (or sites) which is an enormous number! In addition to offering more addresses, IPv6 also implements features not present in IPv4: it simplifies address assignment, network renumbering and packets processing.
In fact, a proper IPv6 firewall requires quite some processing power and RAM, so it’s no wonder that many of the cheap routers don’t have that functionality at all (or it’s not working properly).
The remediation is relatively simple: Just disable IPv6 on the router. In most cases, this shouldn’t have any impact on other services, unless they require IPv6 (in which case, it would be good to replace the router with something better which is IPv6 certified).
Avast Internet Security and Premium products offer full support to IPv6 for your computer on our silent firewall. Take into account that other devices, like network drives connected to the router won’t be protected.
Avast Software’s security applications for PC, Mac, and Android are trusted by more than 200-million people and businesses. Please follow us on Facebook, Twitter and Google+.