It’s been a while now since Tor became the go-to option for those who wanted to ensure their privacy while browsing online. If you still haven’t heard of it, it’s a network that allows you to browse the Internet anonymously, integrated by nodes all over the planet. Each one of this points is actually a computer belonging to a member of the project, which was launched in 2002.
Every one of the machines that is connected to this network sends information securely – all communications are encrypted and the messages pass through random nodes, which makes it very difficult to intercept them or find their origin.
Luckily for lovers of this system, Facebook has announced that it will add Tor to its Android app, which means that those who use it can surf the social network in a more secure manner.
The first steps towards the integration of Tor were seen in 2014, when Facebook launched its onion address. It was an historic move which allowed Tor users to connect to the platform anonymously. “It provides end-to-end communication, from your browser directly into a Facebook datacenter,” explained Facebook.
The launch of the Facebook Tor hidden service also marks the first time a CA has issued a legitimate SSL cert for a .onion address.
— Runa A. Sandvik (@runasand) October 31, 2014
Back then, Facebook also mentioned that they would enable a platform with the same .onion extension for those that chose to connect via their mobile device.
In little more than a year, the number of people who use the Tor service on their computer to enter Facebook has exploded. This, along with the numerous petitions that Facebook received requesting new security features, has brought about this enabling of the system for smartphones.
Accessing Tor from a mobile device is done via the Orbot app, which allows the user to send encrypted information via the anonymous network every time that they connect to the Internet on their mobile.
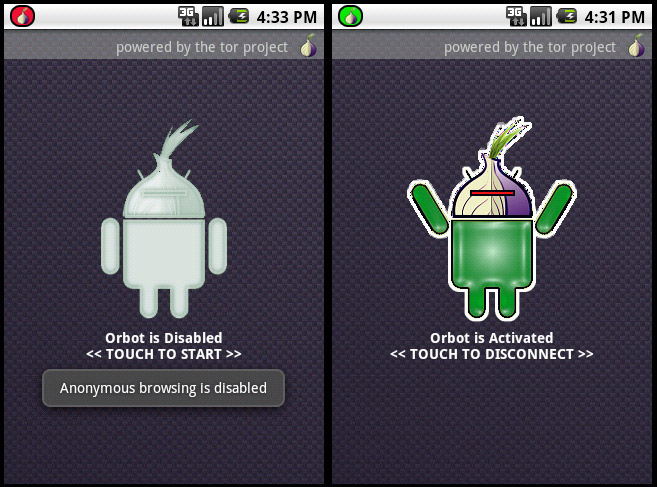
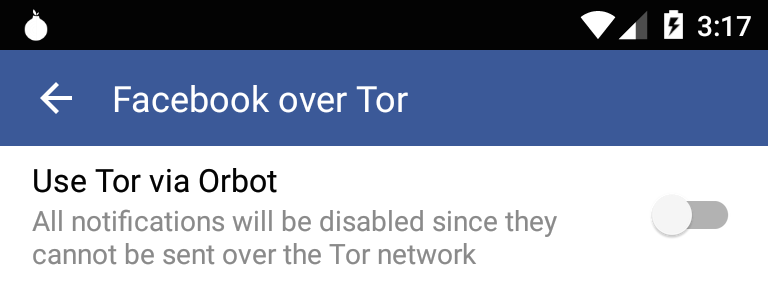
Therefore, whoever wants to enjoy this new service will have to install Orbot on their device. After that, they must enable access to this tool in the settings of their Facebook application so that it can open via Tor.
“We’re releasing this feature over the next few days to seek feedback which will help us create a great experience for using Facebook over Tor on Android,” claimed Facebook on their website.
The project, as they’ve indicated, started thanks to an intern who worked at Facebook for a summer. The Care and Protection team based in London continued with the initiative, which will soon be available to try out by all of us.
The post Facebook strengthens its app for Android, allowing for anonymous browsing with Tor appeared first on MediaCenter Panda Security.